PC Matic SuperShield Protects Customers from Emotet Banking Trojan
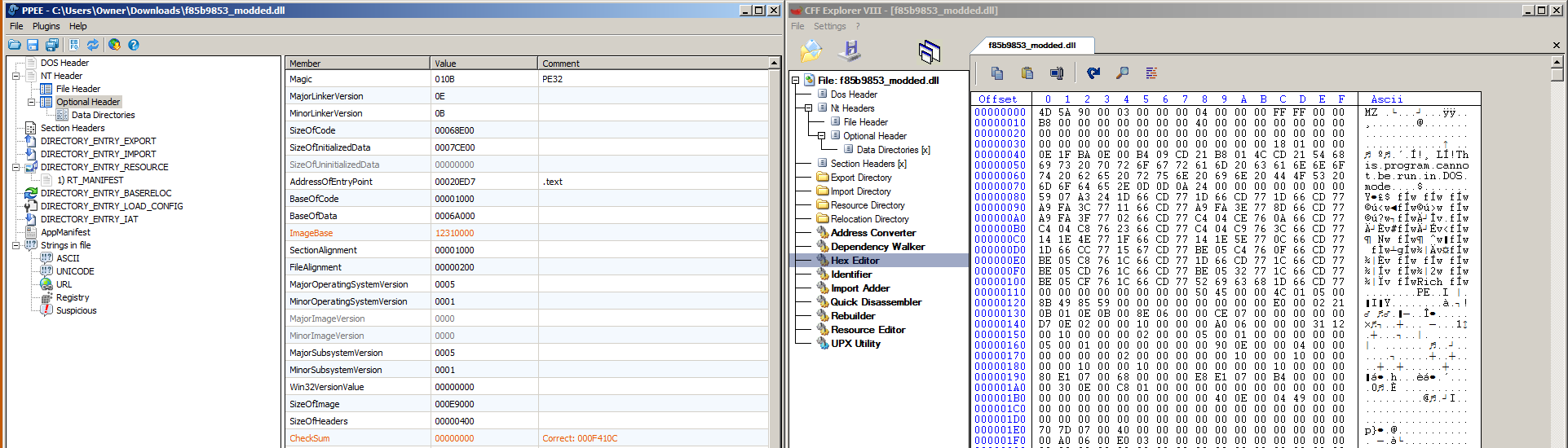
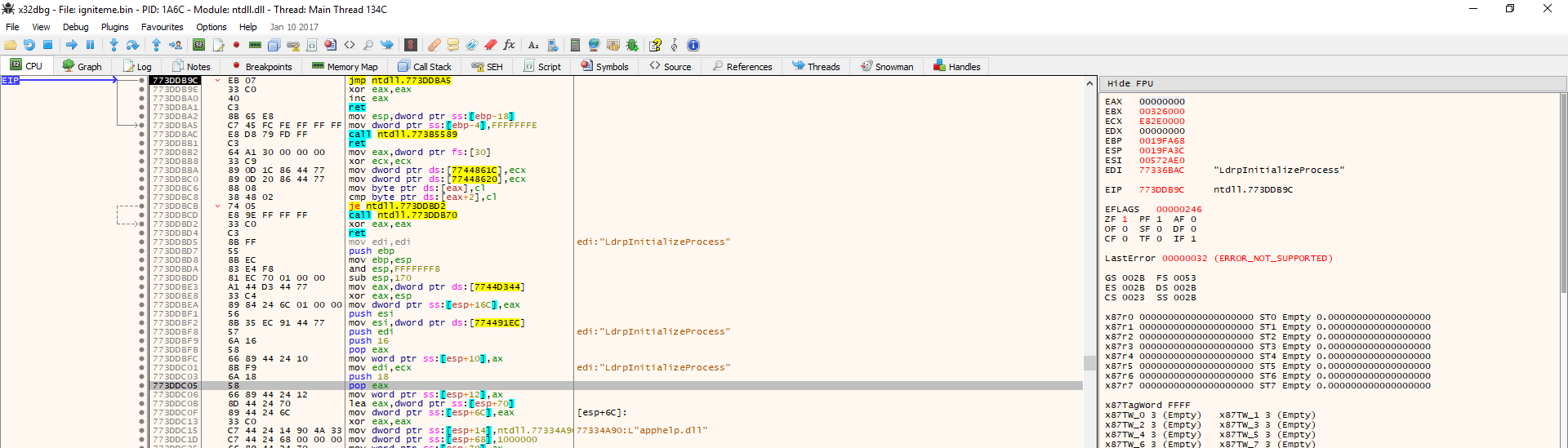
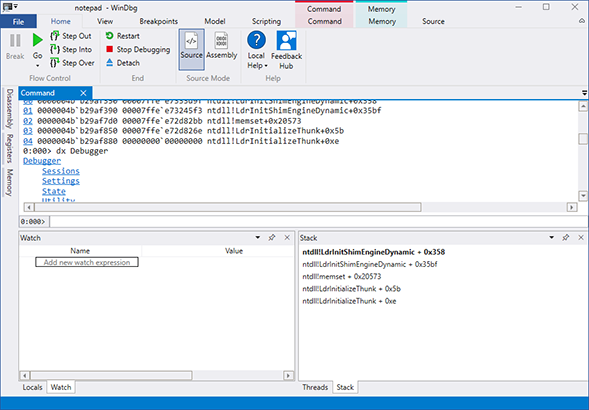
The Malware Research team here at PC Pitstop has noticed a large number of hits on seemingly randomly-generated files in our research queue. Upon further investigation, it is apparent that these files are coming from Emotet Banking Trojan. In this post we will give a brief overview of the Trojan, how we detected it, and […]
PC Matic SuperShield Protects Customers from Emotet Banking Trojan Read More »