Fake tech support companies have been using popups and programs for quite some time with several different justifications to “fix” your computer. Here is a breakdown of a typical tech support scams.
The Hook
In order to have the victim call, there must be a method to force the user to call without looking like ransomware. There are two main methods: web browser popups and disruptive applications.
Browser popups:
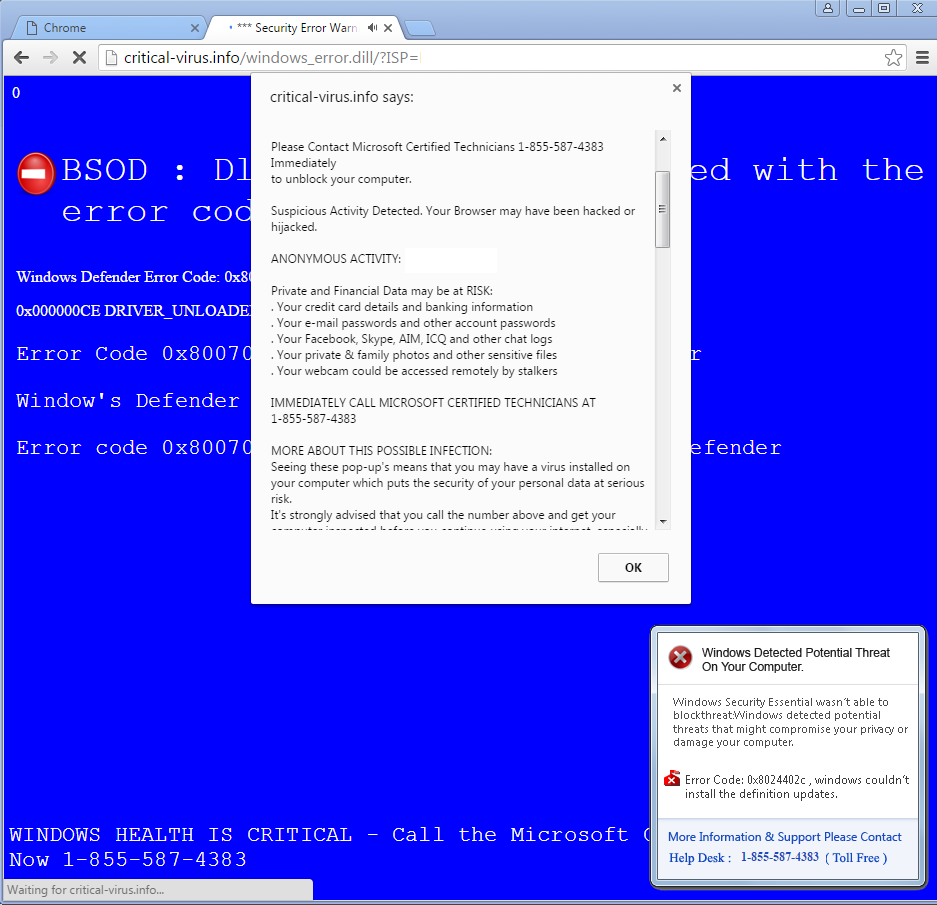
These are the most common method due to the ease of deploying websites to serve the popups. Many of these popups are seen when mistyping website names. When the popups are closed, they are scripted to open again. The easiest solution is to open the task manager(via Ctrl+alt+delete or typing taskmgr) and end the browser process.
Programs
Programs are more difficult for scammers to deploy as they need to be downloaded and executed. These programs can be a little more difficult to close because some of the fullscreen popups try to disable the task manager and block input. Small popup windows can be closed by opening the task manager and finding the offending program which usually stands out.The easiest way to remove the fullscreen window is to know the password which can only be retrieved by calling the scam phone number. Restarting may get rid of the fullscreen popup but some install themselves to startup which means the user will have to boot into safe mode and remove the program.
The Diagnosis
When a scam number is called, they will ask what the error is on the screen. When given, they will tell you one of several problems the computer allegedly has. After that, they will give you a password to close the fullscreen window(if one exists). The “tech support” person will then ask you to download Teamviewer, install it, and give them the connection information. Teamviewer has added a popup warning users about scams and scammers will quickly tell you to allow the connection. After this, they may switch to another remote support application.
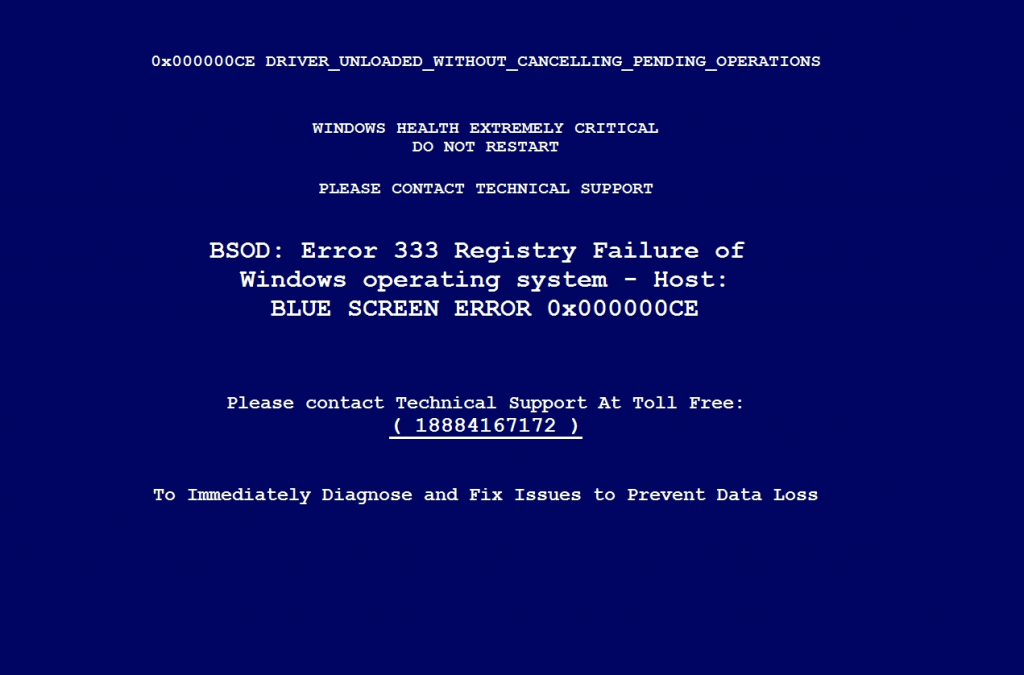
The scammer will use one of several different windows to show “viruses” or other issues. One of the easiest methods is to open the Windows Event Viewer and show critical events. These events can range from unexpected power loss to task scheduler issues but will not notify you of malware.
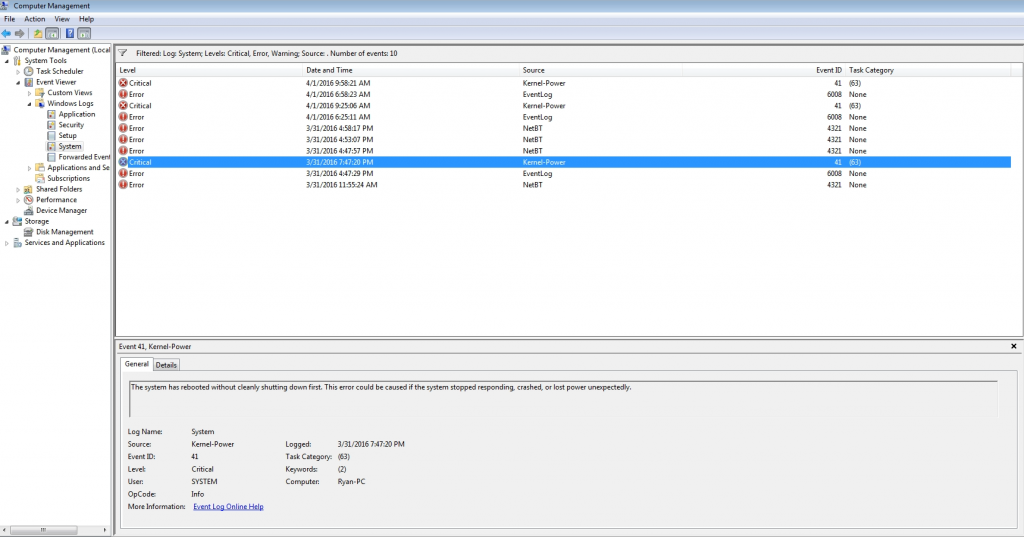
Another scam is to claim Windows is no longer activated. The scammer will show that Windows 7 is installed(if it is installed), open a real Microsoft page that states official support for Windows 7 has ended, and then claim the user needs to purchase a new license key. Neither of these are connected. Windows activation checks if the copy of Windows is legitimate. Microsoft Windows’ lifecycle determines when Microsoft will stop providing technical support and updates to a Windows version. Windows 7’s mainstream support ended in January of last year and scammers are using this to scare users into needlessly purchasing a new(fake) Windows key.
The “fix”
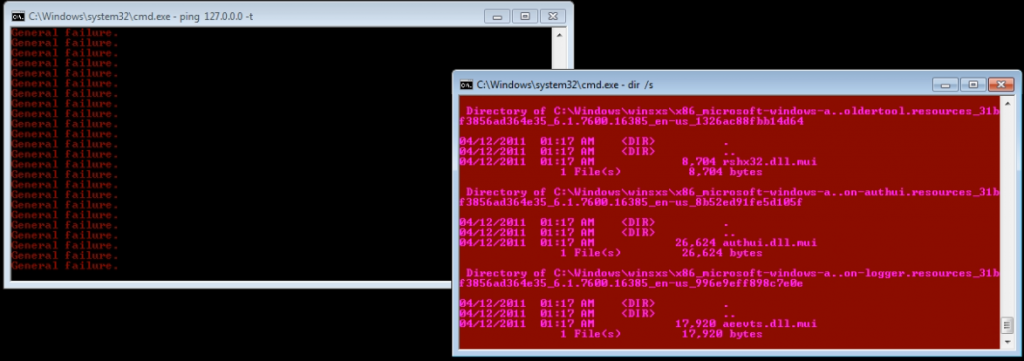
The proposed fix is “removing the viruses” or installing a Windows license key. Scammers are sparse on details of the procedure. These fixes consist of installing AV software and free cleaners. Free software used is typically the most popular cleaners and malware removers. Antivirus software is free or installed using an illegal key. Command prompt windows with scrolling text is sometimes used to add legitimacy and “magic”. These fake windows are very low effort that typically consist of listing the contents of the hard drive and changing the color of the command prompt(Think CSI: Cyber or another popular crime show). If anything, the window listing files will hog hard drive time and slow program installation substantially while it runs.
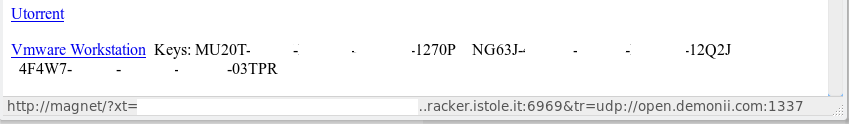
Other software sold is typically pirated and installed with reused keys. One scam company will torrent pirated software from the user’s computer. While very useful, pirated content is often downloaded using torrents due to its decentralized nature.
This section is a little bit light on content, right? Well there is a reason for that. Most of these services don’t do much of anything you couldn’t do yourself with a simple Google search. 🙂
Payment
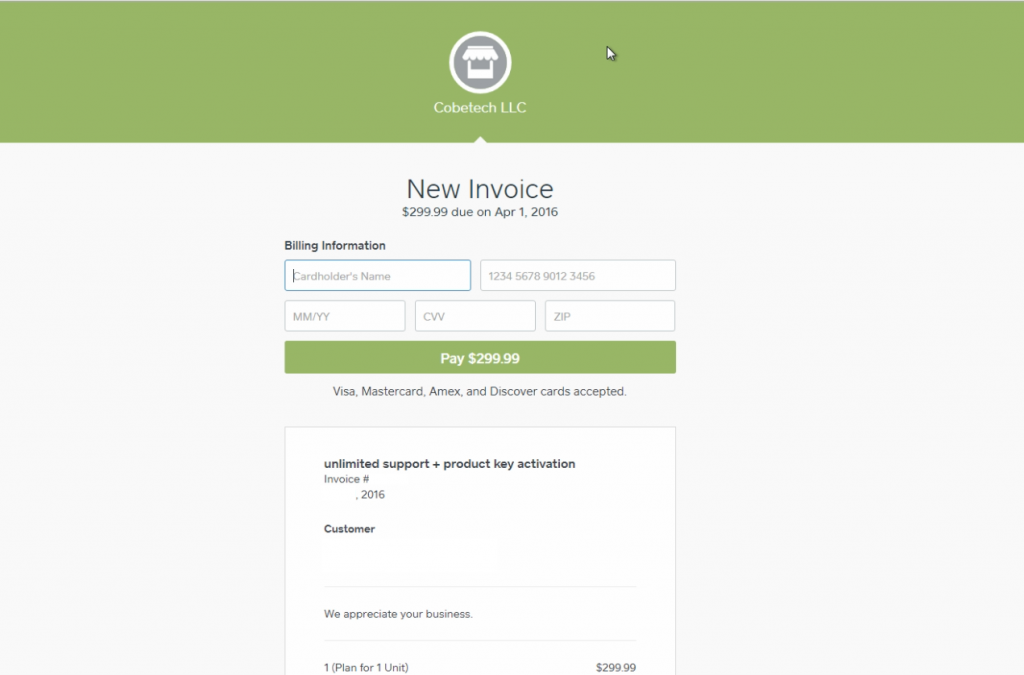
Most scammers will require you to pay before the “repair” starts. Ones that offer to repair first and pay later will threaten to “take legal action” if the caller does not pay. Some of the scams use the reputable squareup.com to collect payments.
Holding hostage
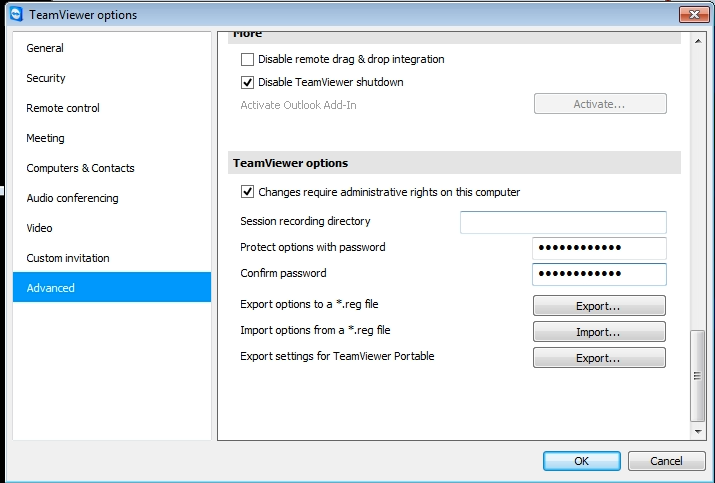
If the scammers “repair” a computer before demanding payment, they will use Teamviewer to keep control of the user’s computer. They accomplish this by password protecting Teamviewer so the normal user will not be able to shut it off. Disconnecting the computer from the internet and uninstalling Teamviewer will generally solve the issue. If not, the user can disable the teamviewer service and terminate the Teamviewer processes.
The Mistake
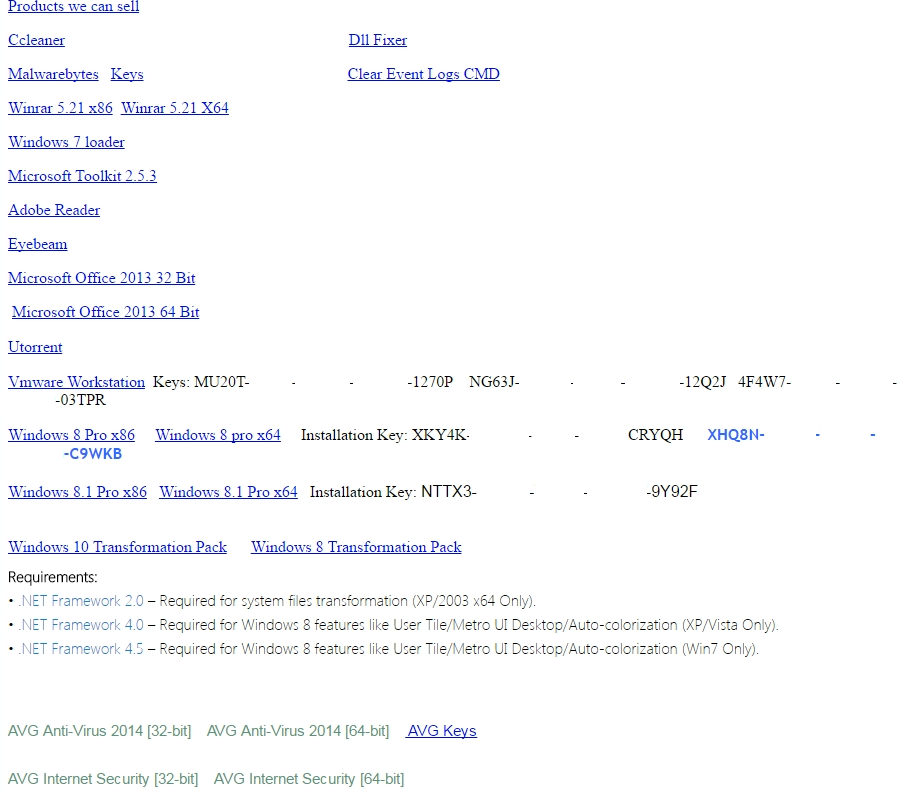
When one of the scammers was pretending to fix the computer, he opened a curious webpage. The page showed download links to the different software they sell and keys they reuse. It also linked to a VMware Workstation torrent and uTorrent installer, further confirming their piracy. They linked directly from other websites for large files and used Dropbox for smaller ones. Someone may be able to report them to Dropbox, Squareup, and the software manufacturers to give the scammers a bad day.