Application whitelisting, also referred to as application allowlisting, application execution control, and software asset management, is a cybersecurity measure that provides only approved applications access to the network and any endpoints on the network. Utilizing a default-deny, zero trust approach to cybersecurity, application whitelisting ensures that any unwanted, untrusted, unknown, or unauthorized applications will not be allowed to execute until they are manually approved, or whitelisted, by the end user’s IT system administrator. By blocking potentially dangerous applications before execution, even the most complex cyber threats and cyberattacks can be prevented in real-time.
How Application Whitelisting Works
Simply put, application whitelisting works by creating a list of approved applications and comparing any new or unknown applications against this list. Typically, comparisons are done by analyzing the file name, file path, file size, digital signature, or cryptographic hash of the application. If an application is not on the list, it will be blocked from running. This can help to reduce the chances of malware being installed on a device or of sensitive data being leaked. Application allowlisting works in an identical manner, except that allowlisting software typically uses more modern approaches that leverage automation and AI to ease the burden that IT administrators deal with when it comes to traditional whitelisting. Ultimately, they work in very much the same way: allow good applications on the allowlist/whitelist, and block the rest.
Five Methods of Application Whitelisting
Application whitelisting works in many different ways, usually in unison with each other, to minimize the risk of malware being executed. According to the National Institute of Standards and Technology (NIST), the five main methods of application whitelisting are:
- file name
- file path
- file size
- digital signature/publisher
- cryptographic hash
File Name
Whitelisting by filename is one of three types of file-based whitelisting, the most common type of application whitelisting, that compares the name of the executable file with the index of whitelisted applications. Perhaps the easiest to get around, this type of whitelisting can be circumvented by simply changing the name of malicious software to that of an application that is allowed on the whitelist. Furthermore, if a known-good or approved application becomes malicious after it’s been whitelisted, it will still be allowed to execute as long as the filename does not change.
File Path
Whitelisting by file path is the second of three types of file-based whitelisting that compares the file path of the executable file with the index of whitelisting applications, similar to filename whitelisting. File path whitelisting is very flexible because it can be configured by directory or by full file path, but this flexibility is also it’s biggest weakness. To circumvent file path whitelisting, cyber attackers can change the path of their malware to match the path of an approved program. In fact, attackers can circumvent file path whitelisting just by placing malware in the same directory as an approved application, even if the rest of the file path does not match. Furthermore, file path whitelisting has the same post-approval issue as filename whitelisting, in which applications that become malicious after approval will still be able to execute because they were previously approved.
File Size
Whitelisting by file size is the third of three types of file-based whitelisting that compares the file size of the executable file with the index of whitelisting applications. File size whitelisting is very similar to filename and file path whitelisting, and has much of the same shortcomings. Typically, all three file-based whitelisting methods are used in unison to provide as much protection as possible. This way, if an attacker wanted to infect a network protected by whitelisted applications, they would need to duplicate a filename, file path, and file size, which can be quite difficult. Even then, it’s still possible, and has been done in many real-world attacks. While this is where most traditional application whitelisting solutions stop, PC Matic takes it a step further to ensure your endpoints are impenetrable.
Digital Signature/Publisher
Digital signatures are essentially watermarks for specific applications created by a publisher. When a new software is created, some publishers may sign the application, which can become a very strong attribute for whitelisting. If a publisher is trusted, their digital signature can be allowed on the whitelist, which will allow all applications, and every subsequent version of each application, created by that publisher to be authorized. While this is a fairly safe and convenient way to manage a whitelist, there is an important caveat to address. Whitelisting via digital signature assumes that because a publisher is known-good, all of their applications are free of malicious code at all times, which is nearly impossible to guarantee.
Cryptographic Hash
Every file has a unique cryptographic hash that is used as an identity for each application. Whitelisting using cryptographic hashes is incredibly difficult, if not impossible, for attackers to circumvent. The main challenge to whitelisting by cryptographic hash comes from the regular maintenance needed to keep the whitelist up to date. Whenever there is a patch management update to an application file, a new file hash is created. Until the whitelist is updated with this new hash, it will be treated as an unauthorized application and will not be allowed to execute. Fortunately, with PC Matic’s global whitelist, we take care of this for you so you never have to worry about continuously updating your index of whitelisted applications.
Application Whitelisting vs Blacklisting
With traditional application blacklisting, which prevents only known-bad applications from executing, application whitelisting undergoes a much more thorough process in evaluating every application and executable before it is allowed to run. Proponents of application blacklisting argue that application whitelisting software is not mature and therefore too complex, too expensive, or unnecessary.
Historically, application whitelisting was seen as an advanced cybersecurity measure that was only necessary in high-risk environments. For most environments, blacklisting was typically thought to be sufficient enough. While this may have been true several years ago, cyberattacks have become so advanced that this is no longer the case, and application whitelisting has even become a baseline in cybersecurity best practices for endpoint security.
Whitelisting solutions and security tools are superior because they stop malware or threat actors from ever running their malicious code on your network or device. Typical blacklist antivirus programs wait until a machine or system is infected or a vulnerability is reported to add malware to their blacklists. At this point, it is already too late and blacklists are attempting to prevent the next attack. Whitelists are malware prevention tools; Blacklists are malware reaction tools.
Application Control vs. Application Whitelisting
Application whitelisting is a security measure that allows only approved applications to run on a device or network. Application control, on the other hand, is a security measure that restricts access to certain applications. Application whitelisting software is designed to monitor entire IT infrastructures, including networks, servers, and operating systems, while application control is typically used on a smaller scale to simply manage application execution. Application whitelisting is also used for more than just applications, and extends to virtually every executable process on your device, including files, scripts, macros, drivers, and security patches. In short, application control is a subset of application whitelisting, and application control software therefore lacks many features and functionalities of application whitelisting software.
Both application whitelisting and application control can be used to prevent malicious software from running on a device or network. However, application whitelisting is generally considered to be more effective than application control. This is because application whitelisting only allows trusted applications to run, whereas application control may allow malicious applications to run if they are not specifically included in the list of restricted applications. As a result, application whitelisting is typically the preferred security measure for preventing malicious software from running on a device or network. While they are frequently used interchangeably, it is important to understand that they are not the same when making decisions about your security stack.
Why is Application Whitelisting Important?
Application whitelisting is important for organizations of all sizes and industries because it helps prevent, not react, to zero-day, malware, and ransomware attacks in an increasingly complex digital world. Fundamentally, application whitelisting also consists of application control, which provides IT admins with significantly more control over what applications are allowed to execute on the network and any endpoints. While individual application management puts an increased burden on IT professionals, there’s no doubt that the extremely high level of protection provided by application whitelisting technologies is well worth the setup. See examples of the numerous benefits of application whitelisting below:
It protects your network and all computer systems on the network
Application whitelisting is a cybersecurity measure that provides a high level of protection for networks and computers. By only allowing approved programs to run on a system, application whitelisting helps to prevent malicious code from executing. This, in turn, reduces the risk of infection and prevents data breaches. In addition, application whitelisting can also help to improve system performance by blocking unwanted programs that may bog down a system. As a result, application whitelisting is an effective way to protect networks and computers from a variety of threats.
It provides full control to the IT team
Application whitelisting is an important tool for IT professionals who need to maintain full control over the software that is being used on their networks. By creating a whitelist of approved applications, IT professionals can be sure that only authorized software is being used. This helps to prevent malicious software from being installed, and it can also help to reduce the risk of data breaches. In addition, application whitelisting can also help to improve system performance by eliminating the need to scan for and remove unauthorized software. Application whitelisting is a powerful tool for IT professionals who need to maintain full control over their networks.
It’s fundamental to cybersecurity frameworks, regulations, and best practices
National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF)
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a set of voluntary guidelines that provides organizations with a risk-based approach for managing cybersecurity risks. The framework is designed to help organizations assess their cybersecurity risks, identify gaps in their defenses, and implement solutions to mitigate those risks. The NIST CSF is based on a set of five core functions: Identify, Protect, Detect, Respond, and Recover. Each of these functions contains a set of activities and outcomes that organizations can use to assess their cybersecurity posture and improve their overall security posture. The NIST CSF is not a mandatory standard, but many organizations choose to adopt it because it provides a comprehensive approach to managing cybersecurity risks. Additionally, the NIST CSF is consistently updated to reflect the latest threats and trends in the cybersecurity landscape.
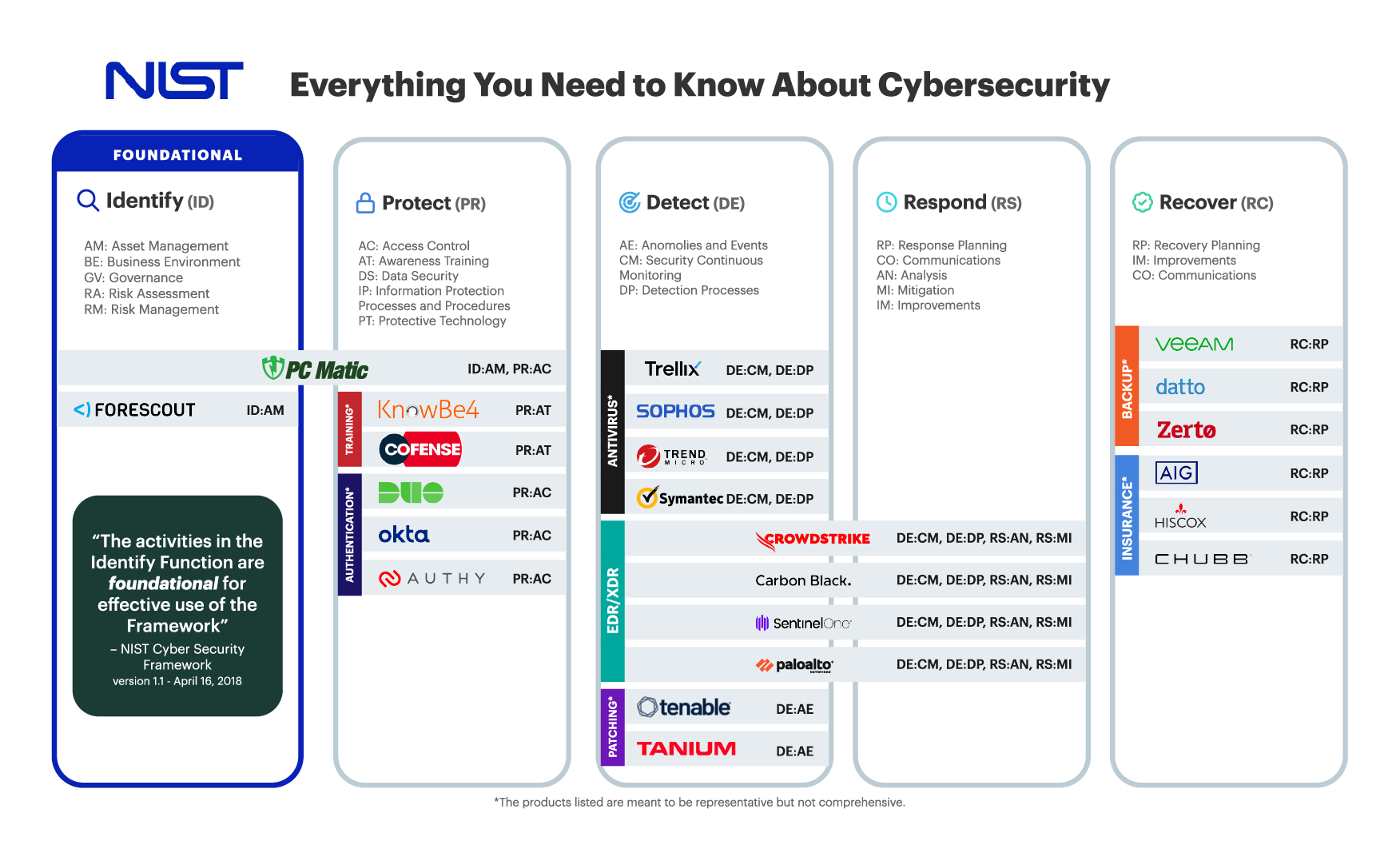
CIS Controls v8
The Center for Internet Security (CIS) Critical Security Controls Version 8, commonly referred to as CIS Critical Security Controls v8 or CIS Control v8, are a set of 18 controls designed to protect against modern cyberattacks on systems and networks. CIS Controls v8 are commonly mapped to nearly every other modern cybersecurity framework and regulation to provide a holistic view of cybersecurity standards designed for the modern digital world. While the fulfilled controls can vary by software, allowlisting typically fulfils Control 2, Inventory of Software, by proactively blocking unknown applications and scripts from executing.
MITRE ATT&CK
The MITRE ATT&CK Framework is a massive knowledgebase of cybersecurity tactics commonly used by threat actors. This framework is unique in that it is the only approach that takes the perspective of the attacker, not the organization seeking to defend against attacks. With that clear, tying application whitelisting to the MITRE ATT&CK Framework can be quite difficult because it can play a major or minor role in several techniques across the matrix. When it comes to mitigations, Execution Prevention is almost entirely fulfilled by application whitelisting software that blocks applications and scripts from executing across the whole environment.
Cybersecurity Maturity Model Certification (CMMC)
The Cybersecurity Maturity Model Certification, commonly known as CMMC, is a certification created by the U.S. Department of Defense (DoD) that sets strict requirements that all DoD partners and consultants must follow to ensure the protection of sensitive and often unclassified information held by the DoD and shared with contractors and subcontractors. The CMMC program has three main detailed requirements that must be fulfilled in order to work with the DoD, one of which is following the Tiered Model – a set of cybersecurity standards. Application whitelisting is one of the most important pieces of the Tiered Model, as it requires strict application execution control.
ASD Essential Eight Maturity Model
The Essential Eight Maturity Model, commonly referred to as Essential Eight, is a term used to describe eight high-priority activities that help organizations protect themselves against cyber security threats. The activities are: application control, user activity monitoring, data protection, access control, contraception, vulnerability management, incident response and recovery. By implementing these activities, organizations can significantly reduce their risk of being breached by sophisticated cyber criminals. The term was first coined by the Australian Cyber Security Centre (ACSC), and has since been adopted by many other governments and security organizations around the world.
Cyber Essentials
Cyber Essentials are a set of guidelines recommended, and often required depending on the type of business, created by the National Cyber Security Centre, a UK government organization similar to NIST. Application whitelisting software fulfils many requirements of the Cyber Essential guidelines, but most notably it fulfils User Access Control and a Default Deny approach to Malware Protection.
Application Whitelisting Challenges
While our global whitelist has a 99.996% success rate, it is not perfect, and it likely never will be. While extremely rare, it is possible for threat actors to create a malicious application that “looks” like a known-good application by duplicating the file name, file path, file size, digital signature, and/or cryptographic hash. Furthermore, social engineering attacks can easily bypass all security measures, and application whitelisting is no different. In these events, it is important to have a complete security stack that will help detect and respond to threats.
Application whitelisting software requires proactive maintenance – you cannot set it and forget it. Traditional application whitelisting solutions have put a heavy burden on the workflows of already over encumbered IT professionals. Our solutions address this issue head-on with our patented list of global whitelisted applications that is updated 24/7/365 by our expert team of malware researchers that are fully operated and managed in the United States. Think of them as an extension of your IT team that is constantly evaluating every single new application for vulnerabilities.
Best Practices for an Effective Whitelisting Process
Implementing an effective whitelisting process is the best way to secure your network and data. But how do you go about setting up a whitelisting process? Here are some best practices to keep in mind:
Before Implementation
First, make a list of all the applications that are essential for your business. This will be the baseline for your whitelist. Next, develop a policy for managing and approving applications. This should include who is responsible for approving applications, as well as how and when new applications will be added to the whitelist. During this process, feel free to reach out to our onboarding team or customer support if you have any questions or need assistance.
During Implementation
Once you have your policy in place, it’s time to start implementing it. Begin by performing a full audit of your network to ensure nothing malicious is currently being allowed to execute. Next, block all applications that are not on the whitelist, both on-prem and cloud applications if applicable. This can be done across the board, per department/group, or per user to ensure everybody has the right permissions for their job function. Then, implement your approval process for adding new applications to the whitelist.
After Implementation
Finally, periodically review the whitelist to ensure that it is still relevant and up-to-date. We recommend regular audits of your network to check for possible vulnerabilities, or you can utilize our built-in reporting tools to get real-time information about blocked applications, new RDP sessions, quarantined files, and more. Finally, stay up-to-date with cybersecurity trends and constantly look for ways to improve your security stack.
Protect Your Network
Free endpoint protection services like Microsoft’s Windows AppLocker just aren’t good enough to protect your enterprise against modern day malware attacks. PC Matic keeps your environment safe, period.
Proactive Whitelist Technology
Our whitelist is much more comprehensive than traditional application whitelisting solutions, has been tested with 99.996% good file accuracy, and consistently blocks more unknown malware and ransomware than traditional blacklist and heuristic solutions. Our patented whitelist consists of:
- Global App Whitelist: An automated global white list of trusted applications that each endpoint can check and update in real-time.
- Local App Whitelist: Customized applications can be added locally with a simple click to the automated global whitelist.
- App Signature Whitelist: Good signed applications are added via the publisher’s signature eliminating the need for whitelisting hashes for past and future applications.
- Malware Script & Macros Whitelist: A trusted scripts and macros whitelist prevents unauthorized execution via valid scripting apps and programs such as Microsoft Office.
- Device Authentication Whitelist: For Multi-Factor Authentication, a device uniqueness algorithm authenticates a user’s device rather than a mobile phone number as a second factor.
- RDP Port Access Whitelist: Secure RDP Whitelist authenticates entering devices to close any security hole preventing ransomware breaches through RDP ports.
Advanced Malware Research Based 100% in the U.S.
By being a PC Matic customer, you instantly gain access to a team of malware researchers that are evaluating millions of new threats 24/7/365. Think of us as your own personal cybersecurity team or an extension of your existing team, but you don’t pay any additional costs.
Stop Ransomware In Its Tracks
Ransomware is quickly becoming a global epidemic for businesses that rely on technology. PC Matic enforces anti-tampering protections at each device to ensure our whitelist security is always in place and able to block even the newest ransomware.
Small Physical Footprint
PC Matic has a small physical footprint on each device. In testing with AV-Test, our product had the lowest impact among AV solutions on download time, run time, install time, web load time, and file copy time. Slowing users can lead to less productivity and more IT calls.
Manage Everything From One Place
With a single cloud based console, you can secure all of the devices on your network while also leveraging an Integrated VNC, Remote CMD Prompt, File Manager, Remote Shutdown and Reboot, RDP Port Scheduling, and more.



