Cerber ransomware, one of the most widely used ransomware, has created a new variant after Trend Micro provided decryption tools for their first version…
Cerber has released Cerber v2, which is not decryptable with any of the decryption tools that are on the market. Cerber v2 has a few modifications to the original Cerber, including:
- New file extention of .cerber2 instead of .cerber
- Implements the CryptGenRandom Microsoft API to generate encryption keys, which is 32 bytes long instead of the previous 16
- Configuration prevents execution on any PCs that have security software such as Avast, BullGuard, ESET and more
- Configuration prevents execution if the OS language is any of these: Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, and Uzbekistan
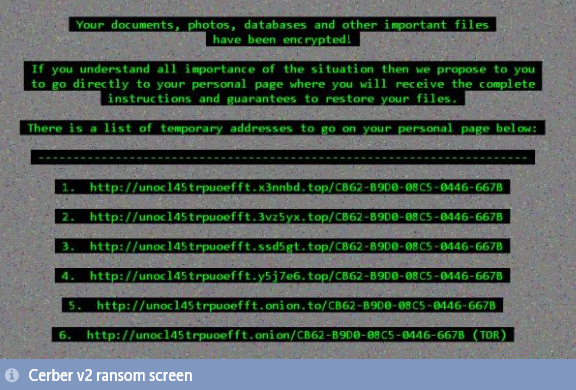
According to Softpedia, the Cerber V2 variant targets 456 different file types, making it one of the most broad ransomware attacks executable. Cerber v2 also updated their ransom screen, see below.
Here are a few tips to prevent being the next ransomware victim. First, think before you click. These hackers are good. The email or notification they send you may look legitimate, but you need to ask yourself if you really should open it. For instance, did you really order a package that they’re saying they can’t deliever? Or apply for a job that they said your resume is attached to? Do you know the sender? Are you expecting the email, etc.
Second, confirm you are using top-notch security software. You need something that is going to block ransomware attacks before they execute. The US-CERT recommends using a program that implements application whitelisting technology. Both PC Matic for home users, and PC Matic Pro for business use, implement this technology.




