Latest Cyber Weapon — Petya or Not?
The cyber industry has been going back and forth for the last week and a half over the latest cyber weapon, deemed NotPetya by some, and Petya by others. Some researchers believed the cyber attack that initially targeted Ukraine was a variant of the ransomware, Petya. Others believed it was a cyber weapon created for data destruction, not ransomware, and called it NotPetya. The creators of Petya even offered to help, those infected, restore lost files with a specific decryption key. Although, it was believed this gesture was to reaffirm the public, they were not involved in the latest cyber attack.
However, The Verge reported there is now evidence NotPetya was indeed created by those responsible for Petya. The cyber criminals responsible for the most recent cyber attack have made a public statement, stating they will provide a decryption key to those infected for 100 bitcoin. As of today, July 6th, that converts to $258,900 USD. Although, the likelihood of anyone paying that amount is slim to none, as most businesses have resolved the issues associated with the attack.
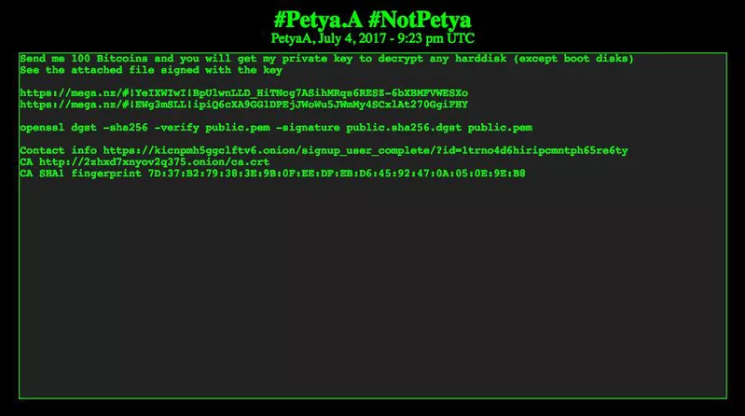
Photo: The Verge
What does this mean?
The message includes a file signed with Petya’s private key. Since their private key was included, it appears the cyber attack was indeed created by the Petya group. It also says in the letter that the decryption key will only work on the hard disk, not boot disks. Meaning, not all files will be retrieved. NotPetya, or Petya, whichever you’d like to call it, was clearly a cyber weapon meant for destruction. A true ransomware attack would only encrypt files that were able to be decrypted at the time the payment was received.
We will continue to keep readers posted as more information surfaces.




