
Zero Trust in Practice: Real-World Lessons
When discussing cybersecurity strategies like Zero Trust, it is easy to get lost in high-level theory. However, the most valuable insights often come from those

When discussing cybersecurity strategies like Zero Trust, it is easy to get lost in high-level theory. However, the most valuable insights often come from those
Subscribe to our newsletter to get cybersecurity tips & tricks and stay up to date with the constantly evolving world of cybersecurity.

The CIS Critical Security Controls are a collection of cybersecurity practices, principles, and defensive actions. They’re provided by the CIS or Center for Internet Security,

In late March 2023, PC Matic was alerted to malicious activity coming from 3CXDesktopApp, a phone system software created by business communication software developer 3CX.

When it comes to cybersecurity software, finding the right solution can be a very difficult task, which is especially true for MSPs, resellers, and affiliates

There are a lot of good reasons to switch to a managed service provider. Most people, and businesses, know about the benefits of having a

If you’re one of the millions of business owners that uses Linux, you already know that Linux servers are cost-effective, versatile, and supremely flexible due

When it comes to cybersecurity breaches, timing is everything. The faster you can detect and solve a digital breach, the safer your brand – and
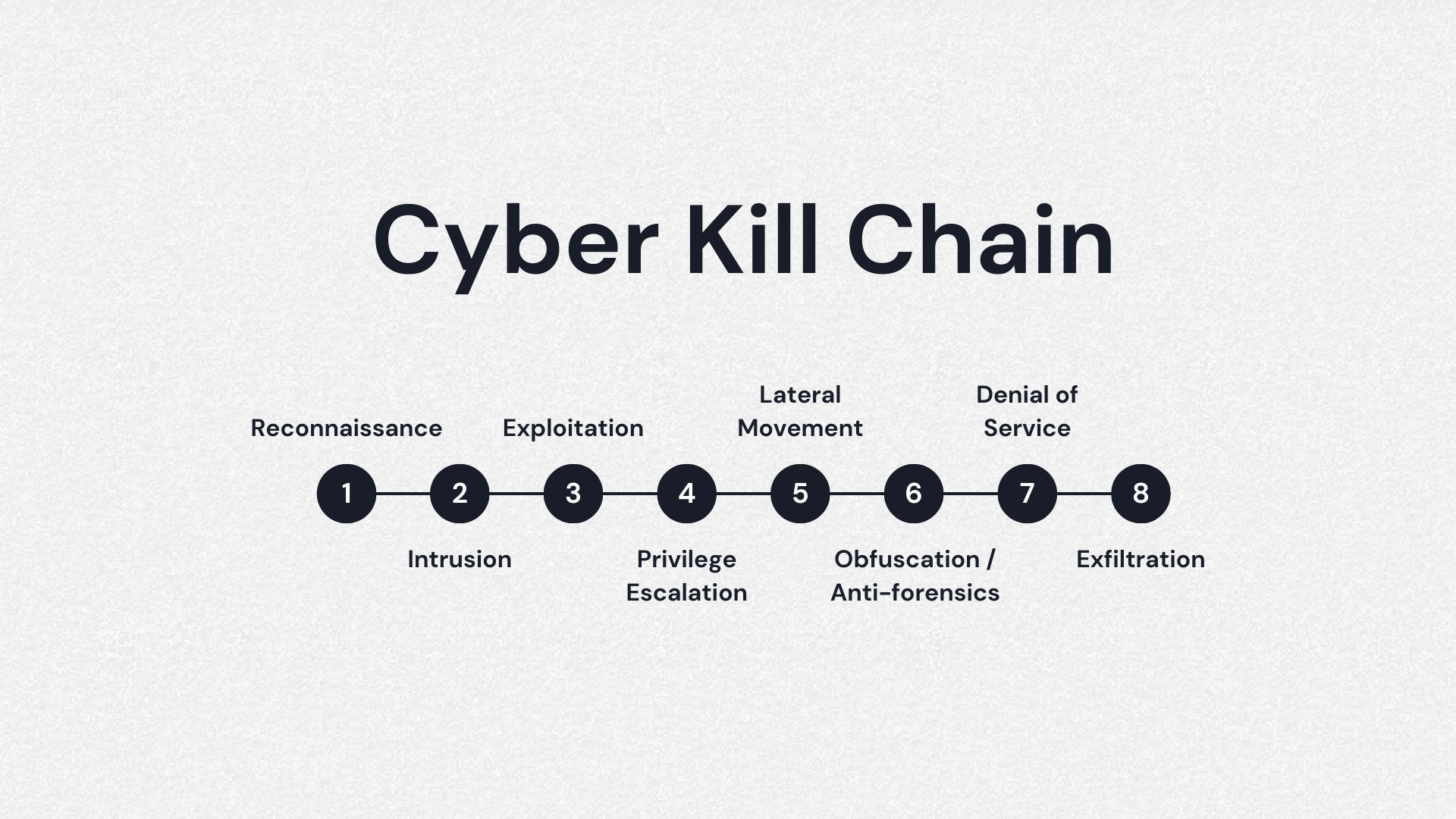
Modern cyber security is an ever-evolving, adaptive process. Because malware and other digital threats constantly change and improve, cyber security efforts, processes, and technologies must

Your organization needs high-quality, responsive cyber security. But to achieve and maintain good cyber security practices and results, you need to leverage in-depth, comprehensive security

Application whitelisting, also referred to as application allowlisting, application execution control, and software asset management, is a cybersecurity measure that provides only approved applications access