International Deliveries in Limbo – How Royal Mail Could Have Avoided Ransomware Attack
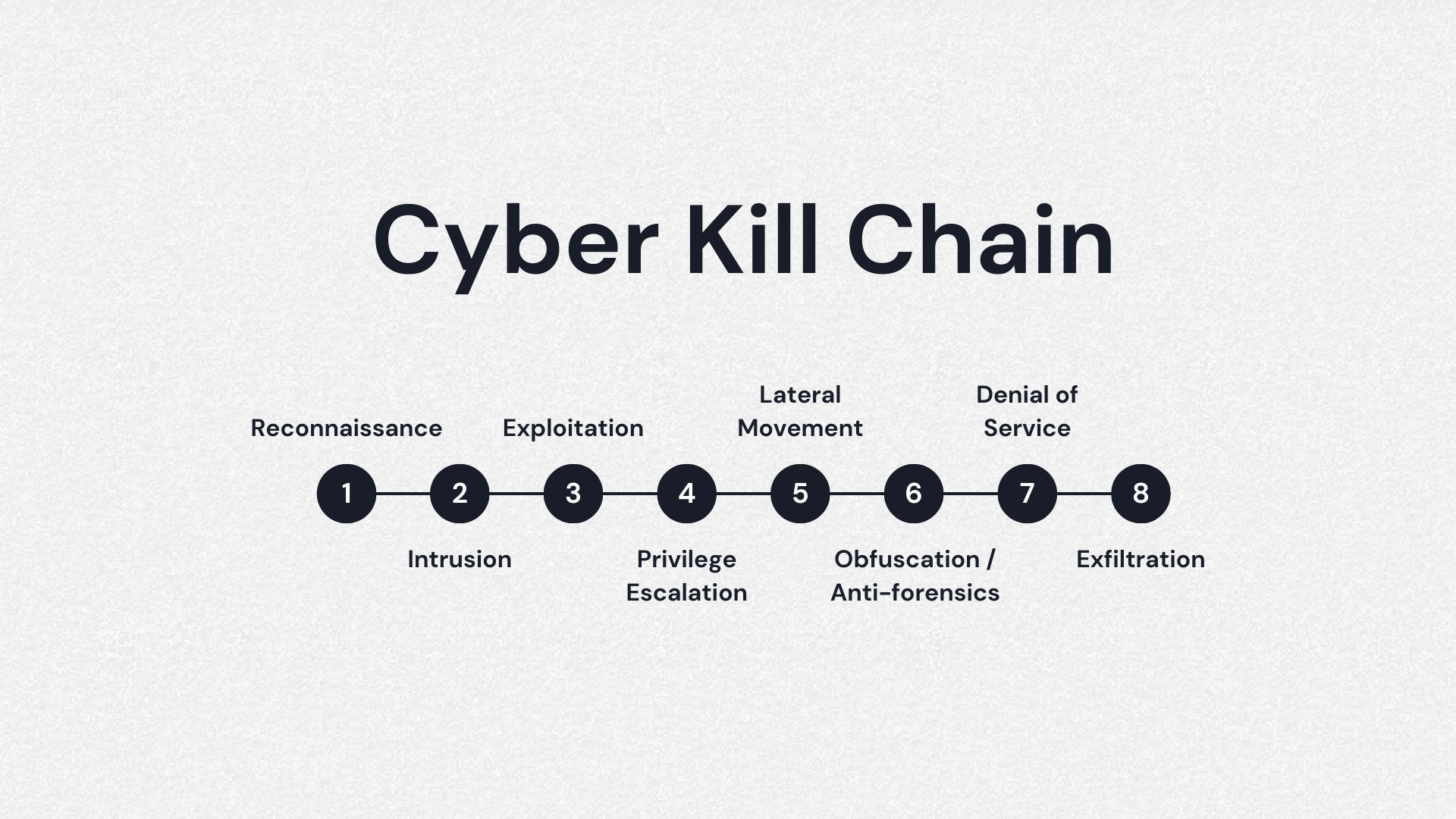
Back in January, it was reported that the UK’s primary postal service and courier company, Royal Mail, halted all international mail and parcel deliveries due to a ransomware attack by Russian-backed ransomware gang, LockBit. The incident, confirmed by Royal Mail CEO Simon Thompson, caused severe service disruption and left businesses and customers feeling the financial […]
International Deliveries in Limbo – How Royal Mail Could Have Avoided Ransomware Attack Read More »