Oahu Man Falls Victim to Ransomware Attack
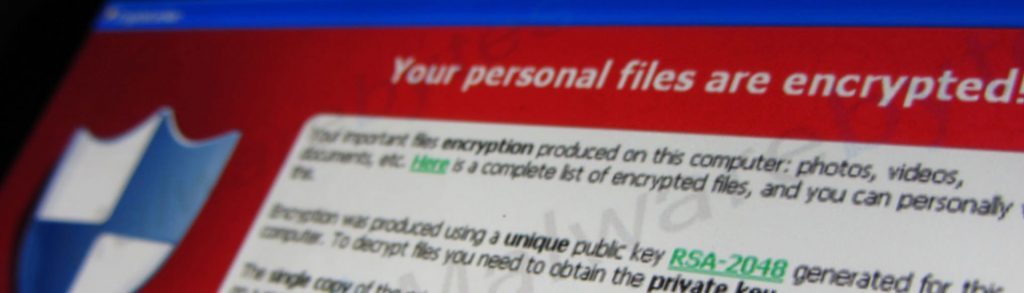
Ransomware Victim Pays $599 and Remained Hacked After clicking on a malicious ad, an Oahu man found himself the victim of a ransomware attack. The man clicked on the ad, to immediately have his files be encrypted by the cyber criminals. The ransomware message from the hackers, displayed a support phone number for the victim […]
Oahu Man Falls Victim to Ransomware Attack Read More »