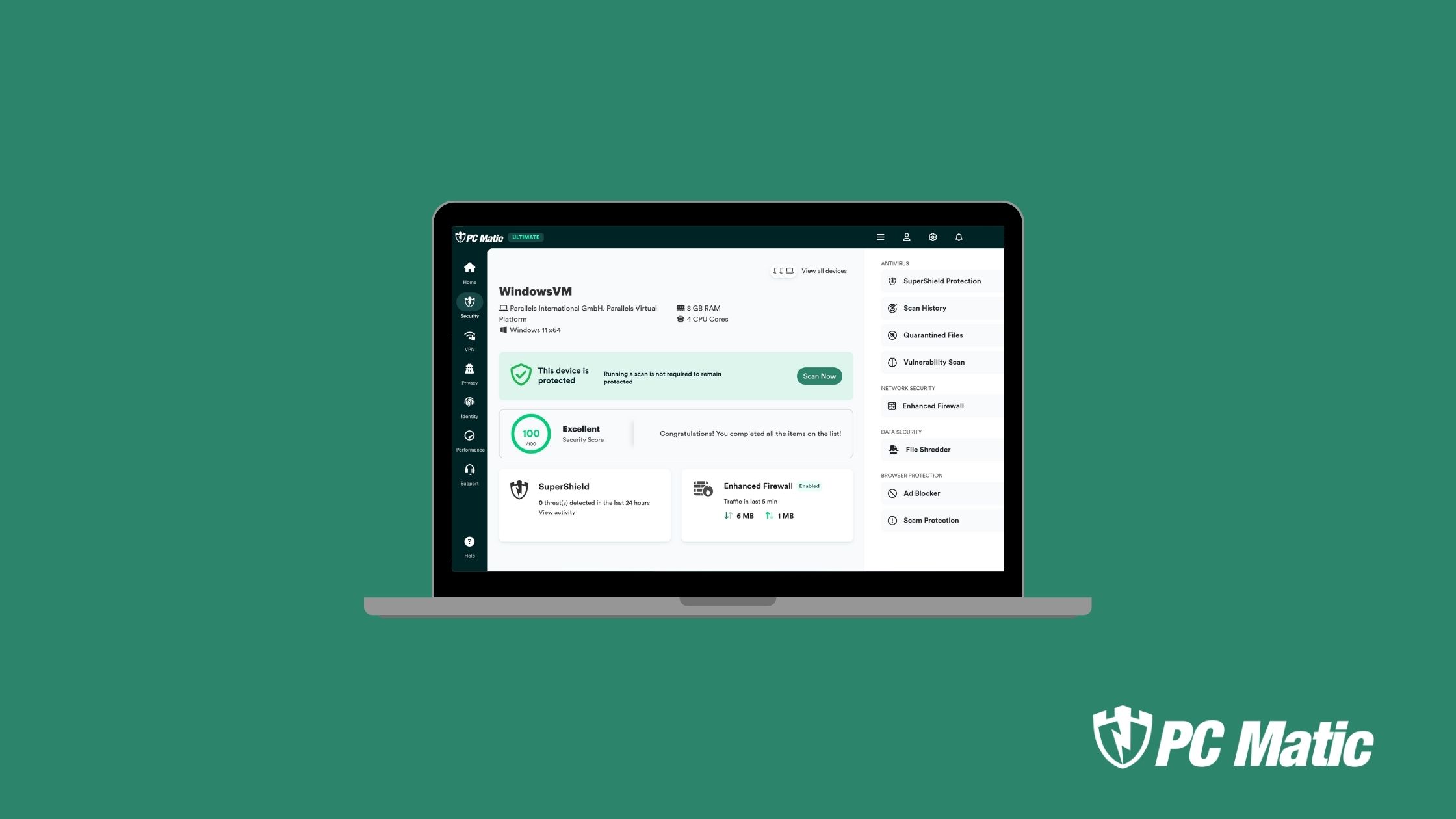
Application Allowlisting: The Critical Security Tool for CMMC Compliance and Modern Cyber Defense
In the evolving world of cybersecurity compliance, one concept is rapidly gaining traction among federal contractors and small businesses alike: application allowlisting. While often overlooked due to its perceived complexity, allowlisting is emerging as a foundational requirement, especially for those seeking to meet the Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC). In a […]