Download AV 2009 now.
Each week I see computers hog tied by Trojans masquerading as AntiVirus and Protection software. Sometimes it’s a neighbor and sometimes it’s a friend, but the story is always the same. “A pop-up said I was infected, so I downloaded a program to remove it.”
The warnings look real, mimicking Microsoft or well known AntiVirus products. The names sound legitimate.
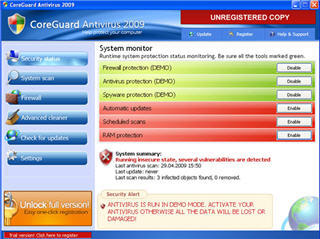
Once you click the link, you’ve been scammed. The link will direct you to buy a product, bilking you of your hard earned cash. Then it scans your computer looking to find more credit and banking information, and you know it will find it.
Can it get any worse? Why sure it can. After you’ve been scammed by false pop-ups, after you’ve paid good money to the very people who gave you the crapware, and after they receive and sell your personal information, they can then connect your system to botnets. Botnets which leave your computer vulnerable to a whole world of scammers and thieves. An automated thief that never tires of passing along your personal information for a profit.
When I tell people what has happened they immediately ask, ” How am I supposed to know what’s real and what’s not?”
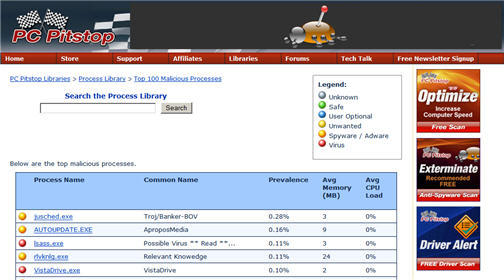
1. Check questionable files. There are several places that offer lists of known malware. Not as many have libraries of thousands of files, malicious or not. PC Pitstop has one of the best. It gives you complete information on malware and safe files. Search the file in our PC Pitstop Processes Library. Use it to identify files that you suspect are malicious. The legend helps determine whether the file is safe, spyware, or virus. There are thousands of files in this list and all have been identified and labeled.
2. Use Google search. This is the quickest and easiest way to check whether a program or process is legitimate. It also requires that you make a judgment on the results you find. You’ll quickly learn to spot key words and phrases like Remove, How To Uninstall, Free Removal Tool. It’s always best to NOT INSTALL a program you can’t identify.
3. Use a good AntiVirus software to protect your system against infections. Be aware that all antivirus software are not created equal. I have compiled a list of reputable and effective software companies that I use and that we suggest through our help desk. Be sure to update the definitions regularly and use realtime protection. These programs work when others don’t. When every minute counts you can’t waste time with products that don’t find and remove the threat.
- Avast from ALWIL **
- AVG
- Comodo
- F-Secure
- Kapersky
- Malwarebytes **
- Norman
- Superantispyware **
Knowing that you’re infected can initially be tough to figure out, but once it takes hold this crapware prevents you from accessing sites on the Internet, particularly sites that could help remove it. Then, as if that weren’t enough, you’ll find you’re unable to download anything. You especially can’t download antivirus software, and if you can download it, you won’t be able to open or run it. CAN’T ACCESS INTERNET, CAN’T DOWNLOAD PROGRAMS, CAN’T INSTALL PROGRAMS, just perfect. Now what do I do?
Take action immediately to remove the already introduced malware. Know that once you see these pop-ups, you are already infected and that taking the wrong steps can only let the infection strengthen. If you wait too long, your system will literally come to a halt. No downloads, no internet access. Yes, these beasts prevent you from accessing the very sites that could offer you assistance with legitimate antivirus removal tools. Eventually there is no escape without spending big bucks to erase your drives and reinstall Windows.
We of course recommend Exterminate but be aware that no single software can cover all threats. Use a minimum of two programs to search out threats. If you would rather take advantage of the free programs available, choose one from those suggested in our Safe Software list above.
If you are experiencing these symptoms please take the following action immediately.
1. Boot into SafeMode With Networking. To do this, reboot your system while continuously tapping the F8 Key.
2. At the Options screen choose SafeMode With Networking.
3. Download each of the following free software programs.
a. Malwarebytes
b. Superantispyware
c. Avast Home
d. Exterminate scan
4. Be sure to update the definitions for each program before running. These threats are changing by the hour and updating definitions is a must. Without updating, you are wasting your time.
5. Once you have downloaded and installed at least two of these, I suggest Avast Home as a second choice, turn off your system restore, and run the antivirus. It’s necessary to turn off system restore because this is a favorite hiding place of Fake AntiMalware. Turning it off allows access to your complete drive. The restore function is usually disabled by the virus anyway so your not loosing anything. Running System Restore when infected only strengthens the trojans hold.
6. If given the option, allow the programs to check memory and boot sector on reboot.
7. I would run each program at least once in SafeMode With Networking and again in regular Windows Mode.
8. When clear, be sure to turn on System Restore and create a new clean restore point.
If fortunate, you’ll successfully remove these threats, but be aware that these nasty thieves are getting better and better at disguising themselves. If ignored for too long, their strangle hold is impossible to break.
____________________________________________________
PITSTOP MALICIOUS PROCESS LIBRARY
LINKS TO FREE AV
PREVIOUS ARTICLE ON CONFICKER WORM REMOVAL




