ScareWare &You
Without a doubt the largest threat to the security of your computer and consequently your identity, and bank account is YOU, followed closely by ScareWare. The best firewalls and most effective antivirus won’t help a bit if you, the user, click on Rogue Security Software and fake warnings. Known also as Scareware, this thief is fooling you big time. When it knocks, do not open the door.
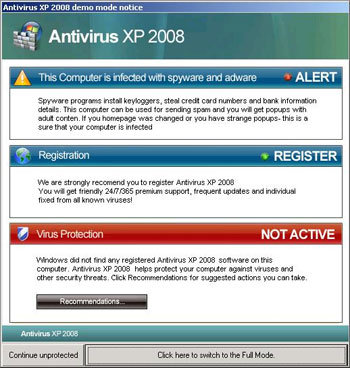
The programmers writing todays scareware are as sophisticated and well paid as any of the Microsoft, or Norton/Symantec programmers. They design software that is indistinguishable from the real thing.
Even the well trained are being duped. Here’s an older Rogue security threat that masqueraded as Microsoft. This one is more than two years old so you can imagine how much better they are now. There is, of course, the same threat with the date changed to 2010 romping around now. Some are hijackers, some are trojans. The architecture doesn’t matter, it’s the damage they do that can ruin your life.
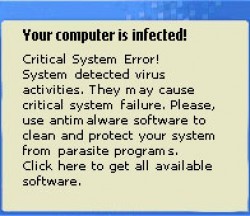
A big part of my day at PC Pitstop is spent in the Customer Service Department helping our customers overcome issues encountered while on their computers. Every day I see people describing ScareWare that has taken over their system. They are unable to run their antivirus because they can’t get to the sites they need. The Rogue AntiVirus has hijacked their browser and will not let them near a site that could help. Not being able to access a site or download a removal program is the work of the infection. The user receives a warning, clicks on a link to download an update and BAM! They’re infected.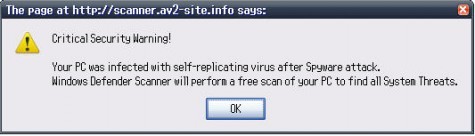
What Do I Look For?
Any warning or suggestion that you are somehow infected is to be treated as possible scareware. You can be casually surfing the web or simply working with a program on your system when these false warnings arrive. Don’t click on them. Just because they’re knocking, don’t let them in. The same is true for any popup suggesting you need to download the latest version of a program or video player. Treat them all as suspect.
Looking for security software? You better know the software your reviewing. Even something as simple as a Google search can produce the very Rogue you are trying to avoid. Just because it shows up in a Google search doesn’t mean it’s safe. If you don’t know it, don’t let it in the door.
How Does It Hurt Me?
The most obvious damage but also the least troublesome, is that it prevents you from using your computer. It wastes your time looking for a way to rid yourself of the pest and get where you want to go. Consider yourself lucky if you realize you are infected and are successful removing it.
The next obvious damage is a little more frightening. It simply steals your money by duping you into buying the rogue program. Your immediate monetary loss may only be a few bucks but do you really think that is the end of it? Do you really want your credit card in the hands of people who duped you to begin with? Do you think they will keep your information safe? Just the thought of it is enough to make me shiver.
What Do I Do?
1.) Don’t click the OK button or any other command that pops up. Immediately hit your CONTROL/ALT/DELETE buttons to enter your Task Manager. Find the process that is giving you the warning and click “End Task”.
2.) Go to Start/Run and type “msconfig” (without the quotes) then click on the StartUp tab and make certain there are no items listed that do not need to be started with Windows. Look for the Rogue problem under StartUp.
3.) Run your copy of PC Matic along with your Free MalwareBytes, and the Free Superantispyware tool. Run all three and if needed you can also run the free version of Avast.
4.) Repeat the process but this time use SafeMode With Networking. The reason for running in Safe Mode With Networking is that the threat may not be active and able to resist removal. This is not always the case and in some cases you will not be able to access SafeMode With Networking.
To access Safe Mode with Networking repeatedly tap the F5 or F8 key while the computer is booting up. Once the menu opens, select Safe Mode with Networking, and if prompted, administrator. The screen will look different because the video driver is not loaded. That will return to normal after a reboot. To run PC Matic, you may need to go to Start>Programs>PC Pitstop>PC Matic if the desktop icons are not present.
If the computer connects to the Internet using a wireless connection, it may be necessary to connect using an Ethernet cable in order to have Internet access from Safe Mode with Networking.
5.) HiJack This: If running all of these programs from Safe Mode with Networking does not resolve the issue, your next step is to scan with the HiJackThis tool and post a log on our website. Get assistance from one of our Trusted HJT Advisors. You can read about HJT here. Post your log here.
There is no one program that removes all threats at all times. If it were that easy the bad guys would have quit long ago. Virus and malware mutate by the minute. What you were protected against this morning is not what is attacking you this afternoon.
One of the things that causes some discussion here is the way to handle Windows System Restore. I’m a firm believer in turning it off before starting the removal process described above. The reason for this is that the virus can hide there. You clean your system, find no more problems but then a few days later you are infected again.
Anytime you turn off Windows System Restore you are taking a risk. I am now suggesting that you follow the steps outlined above and when finished and testing clean, turn off Windows System Restore. Repeat the whole procedure and then turn it back on and create a new single restore point. If you are unable to get a clean scan and have already decided to do a re installation of your operating system, then by all means, turn off System Restore and try the procedure once again.
Good luck and happy computing.
Useful Links
______________________________