Microsoft Database Leaks Unknown Number of Source Codes
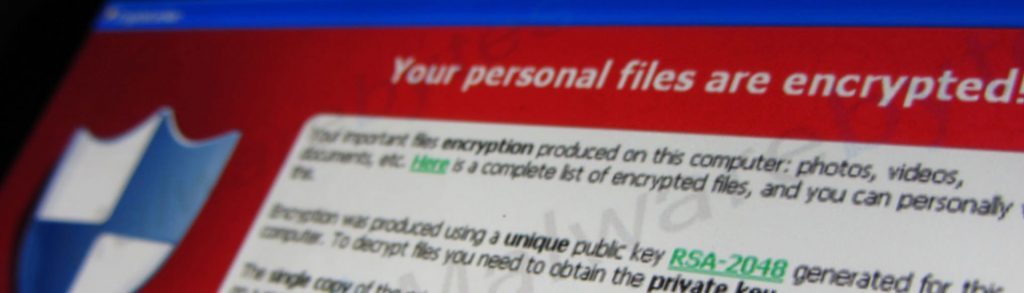
Database Breached – Leaving Microsoft Source Codes Exposed Microsoft recently confirmed an unknown number of source codes were leaked onto a repository named BetaArchive. Exposing the source codes would allow hackers to find vulnerabilities in some of Microsoft’s most trusted pieces of its operating system. Gizmodo reports, “The Register claimed the data dump was 32 […]
Microsoft Database Leaks Unknown Number of Source Codes Read More »