CloudPets Breached Leaving 820k Users Exposed
The children’s toy, CloudPets, has been breached, leaving 820,000 users exposed. This led to an estimated 2.2 million voice recordings between parents and their children being leaked. What is most shocking is just how avoidable this data breach was.
According to Troy Hunt, the platform the toy used, MongoDB, did not require any form of authentication to obtain the stored data. This led to several individuals gaining the ability to obtain the data. The exact number of people who have gained access in unknown.
The company reported to Network World they were just informed of the issue last week by Vice Media. Mark Myers, CEO of the company, stated,
“The headlines that say 2 million messages were leaked on the internet are completely false. We looked at it and thought it was a very minimal issue.”
However, there is evidence suggesting these issues were brought to the company’s attention long before a week ago. Hunt reports there were actually four attempts to contact the company regarding the breach. Below are the screenshots of two of the emails sent to CloudPets, featured on Hunt’s blog,
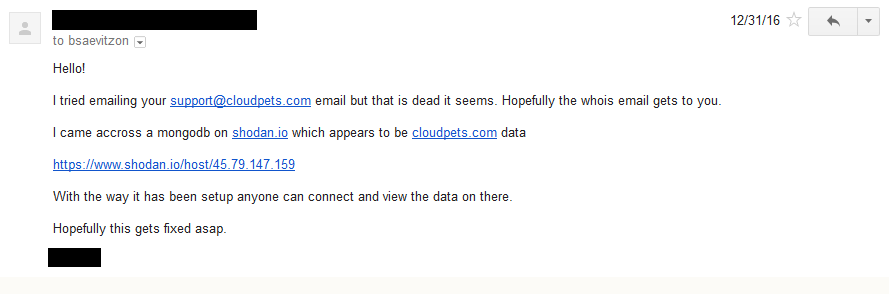
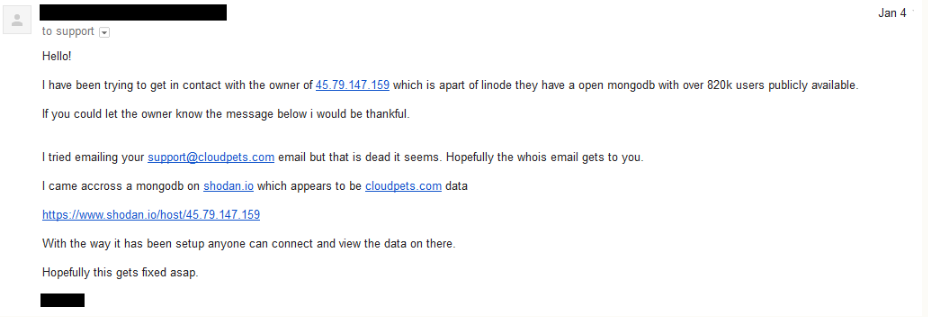
As you can see, the first email correspondence was sent December 31, 2016. A follow-up was sent on January 4, 2017 explaining the magnitude of the issue.
Minimal Issue?
For Myers to refer to a breach as a “minimal issue” is rather bold considering 820K accounts were breached, leading to 2.2M voice recordings being exposed. Also, this data was being held for ransom by the hackers. The ransomware variant used was not released, nor was the specific payment demand. However, several ransom notes were found stating if payment was not received, the data would be deleted.
But It Gets Worse
Hunt did a little more digging, and tested the app used for the toy. He found what he called a “double edge sword”. First, the passwords are encrypted with bcrypt, which is a good thing. However, there are no password requirements. So, you could literally have a password of “1” or “j”. Even using the bcrypt feature, Hunt was able to decrypt several passwords very quickly due to the lack of password requirements. Myers made the following statement regarding the password requirement concerns,
“We have to find a balance. How much is too much? Maybe our solution is to put more complex passwords.”




