Earlier in March Microsoft disclosed several 0-day vulnerabilities within Microsoft Exchange that were actively being exploited by hacking groups. We now have more details about the versions affected and what patches are available for them.
Before we go further if you’re not running an on-prem version of Microsoft Exchange then you can probably stop reading now unless you’re interested to learn patch recommendations.
The Timeline
This is a simplified timeline from a very detailed write-up by KrebsonSecurity that we encourage you to read.
January 2021 – Several groups report findings to Microsoft detailing remote code execution vulnerabilities in Microsoft Exchange which is later confirmed by Microsoft.
Late February 2021 – Attackers begin mass scanning for Exchange servers that are vulnerable and compromising them.
March 2nd, 2021 – Microsoft releases patches for the four 0-day vulnerabilities.
March 5th-7th, 2021 – KrebsonSecurity estimates that 30,000 organizations in the US are compromised by this which is later confirmed by Wired.com.
March 12th – Microsoft still estimates there are at least 80,000 unpatched Exchange Servers worldwide.
The fallout from these vulnerabilities is deeply concerning and still unknown. PC Matic is confident that it’s customer will remain unharmed with SuperShield running and preventing all unknown payloads that could be brought through the vulnerability of a compromised device.
What Versions Are Affected?
Microsoft has released guidance that the following versions of Exchange are affected.
- Exchange 2019
- Exchange 2016
- Exchange 2013
- Exchange 2010
Exchange 2003 and 2007 are not believed to be affected at this time and thus have no patches to apply for this vulnerability.
If you are running one of the versions listed above (2019,2016,2013,2010) you must patch that server as soon as possible. Microsoft has laid out several options for patching that range from a move to the latest CU or applying only the security fixes for this set of 0-days to your current CU. If you’re running Exchange 2010 SP3, you can install this update to patch your servers for the March 2021 incident.
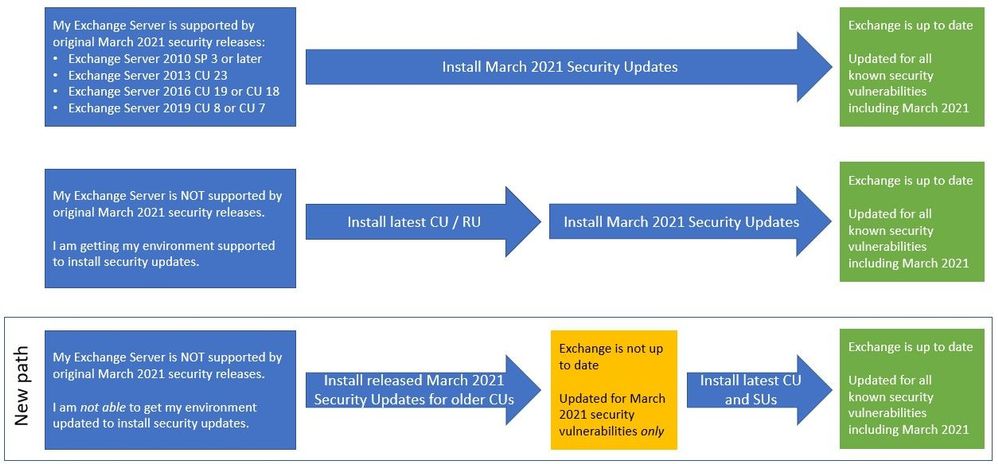
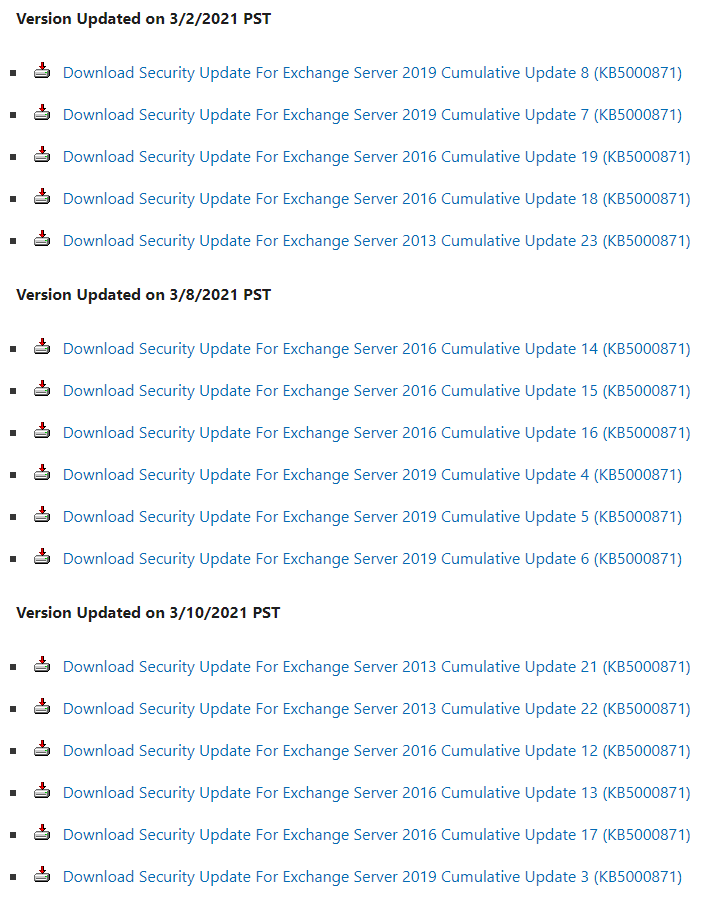
If you cannot currently bring your Exchange server up to the latest CU, visit the Microsoft Download Center section of this page, and find your current Exchange version and CU. You can then download the new release version of that CU and apply the security fixes for what is now known as the March 2021 incident.
What’s next?
Applying the patches from Microsoft is only step 1. It’s important to still look for signs of compromise on any of your exchange servers. There are several write-ups with full details on the attack like this technical article from Microsoft. There you’ll find the attack chain, how you can look for signs of compromise, known hashes associated to compromise, and more.
Again, PC Matic is confident that its customers running SuperShield on Exchange servers will remain secure from any attempts by attackers to deliver payloads to a compromised Exchange Server.