Has your spouse, child, or friend ever used your PC? No problem, right? Until you use it again, and certain desktop icons are missing, or files or pictures have magically disappeared. Its far too common for these errors to happen when someone else is using your computer. Although it can be frustrating and concerning, there are ways to prevent it.
By creating a “Guest” user account, you can allow limited access to your computer without fear of your personal data being erased. For some, it may be best to create multiple users, depending on who is using your PC. For example, a specific user account for each child. To create another user account for your computer, follow the steps below:
Add New Users to PC
First access the Control Panel by going to the Start menu, accessing “All Programs” and finding “Control Panel”. You could also type “Control Panel” into the search bar by the Start menu. Once you access the Control Panel, you will need to click on “Change account type” as shown below.

Upon doing so, the following screen will populate:
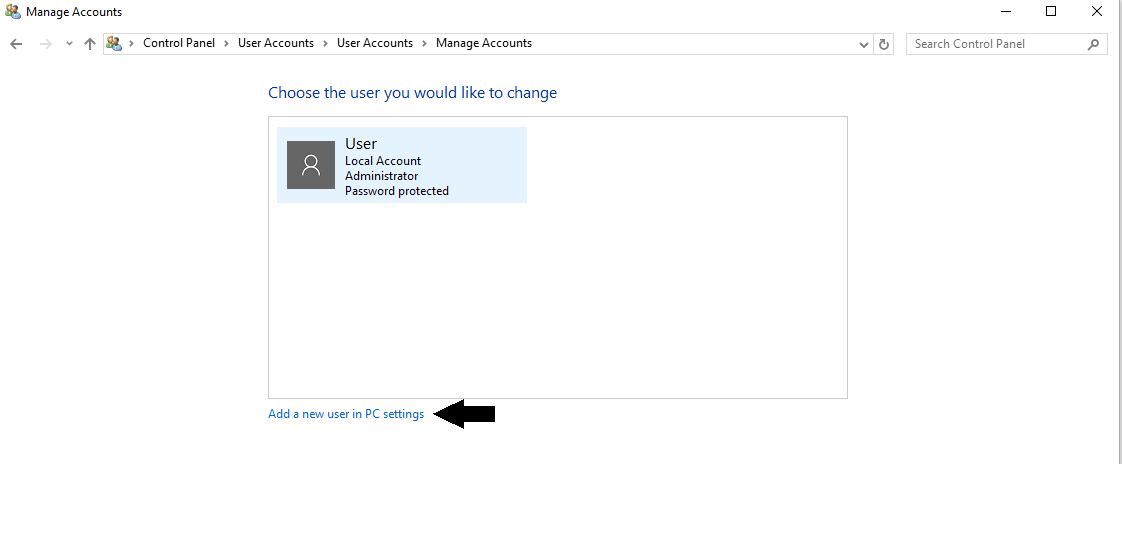
By clicking on “Add a new user in PC settings”, you will be taken to this screen:
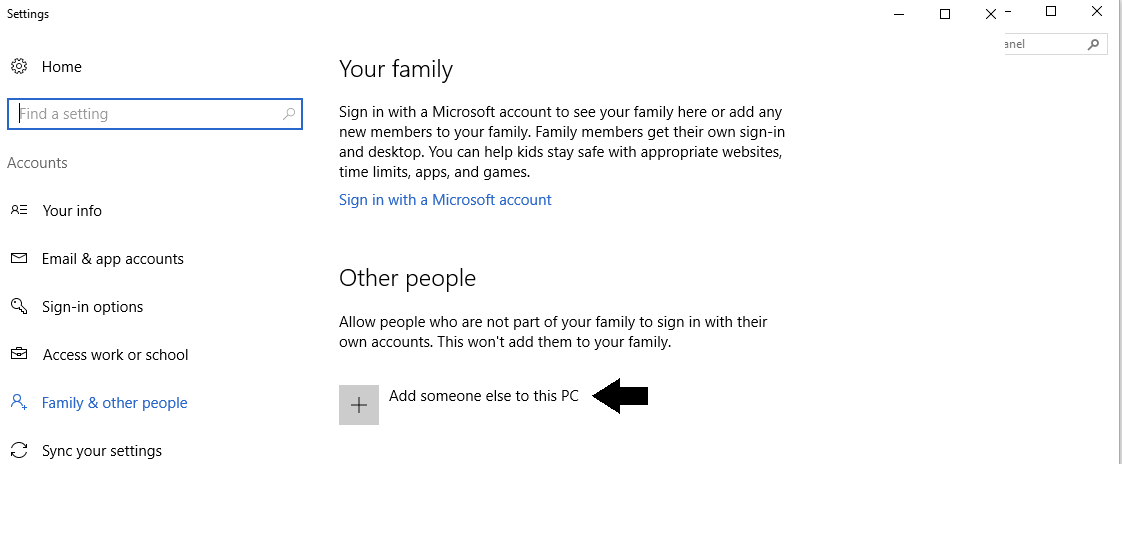
Click on “Add someone else to this PC”. This will bring you to this screen:
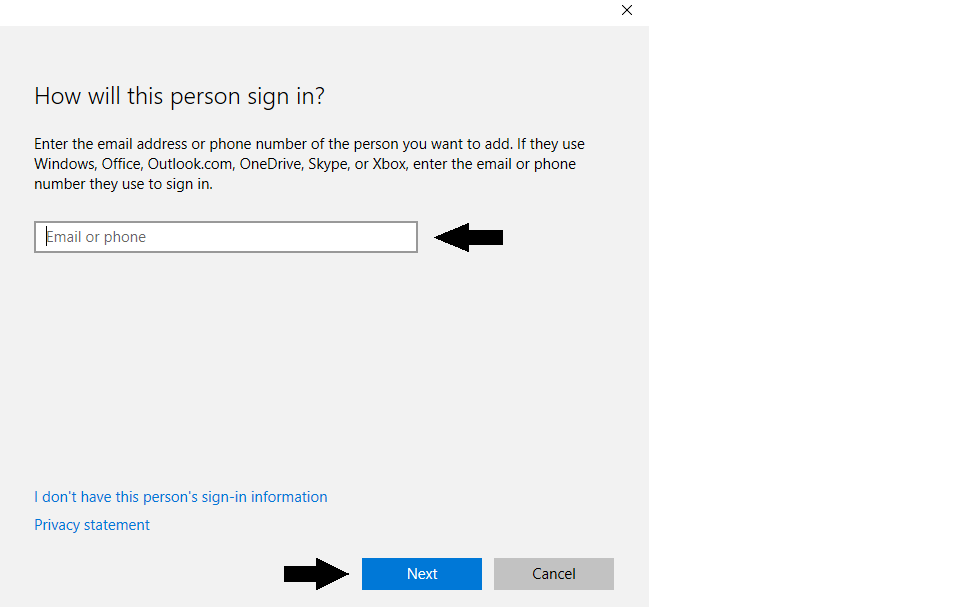
On this screen you will need to enter either a phone number or email address for the alternative accounts. Upon doing so, you can click “Next”. If you are making this primarily a “Guest” account to be shared, you will want to use a phone number or email address that everyone knows but is not tied to any pertinent accounts (ex: online banking accounts, shopping accounts, etc.). Upon clicking “Next”, you will see this screen:
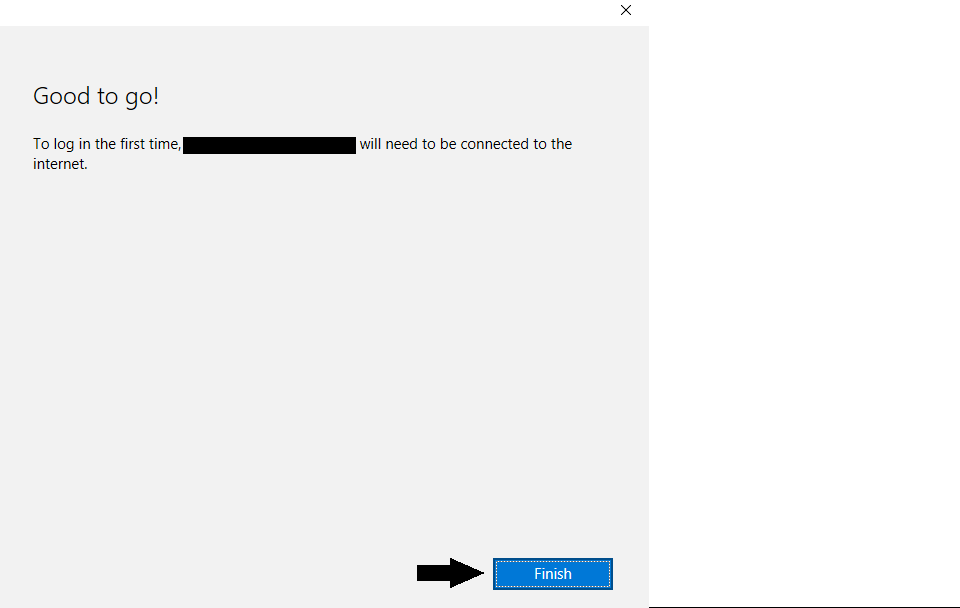
Click “Finish” and you are all done!
Now, these alternative accounts can be used by whomever you see fit, without compromising the primary PC users’ data.




