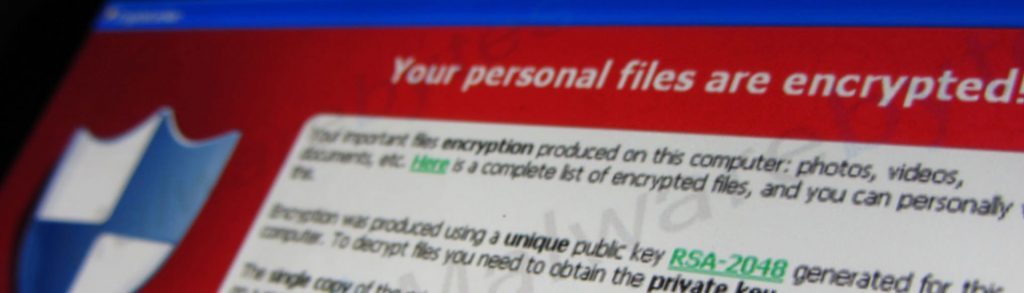
Ransomware, or malicious software that encrypts your files, holding them hostage until you pay the ransom demand, took the IT world by storm in 2016. On many different platforms, I have read about PC users falling victim to ransomware. Many of these cases are certainly true; however some I have found are actually support scams, or other viruses that have overrun PCs. Ransomware, due to its highly publicized nature has become the name of all malware. When it is simply one type, which is being incorrectly categorized at times.
Ransomware – What is it?
The intent of this post is to help users understand what exactly ransomware is. If you have found yourself a victim of ransomware you will have noticed the following:
- First your files are encrypted. This means they are completely inaccessible to you. Perhaps not all of your files were encrypted, but what the hacker deems as “most important” will be on the top of their encryption list.
- Second, you will receive a message from the hacker stating you must pay a certain amount of money, in order to get your files back. The amount varies upon the ransomware variant (the type of ransomware), as well as the victim. For instance a home user will not be demanded to pay as much as say, a medical facility. The demand may look something like these two images.
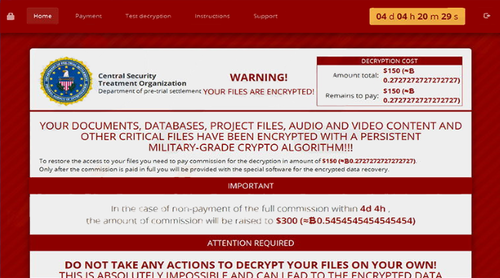
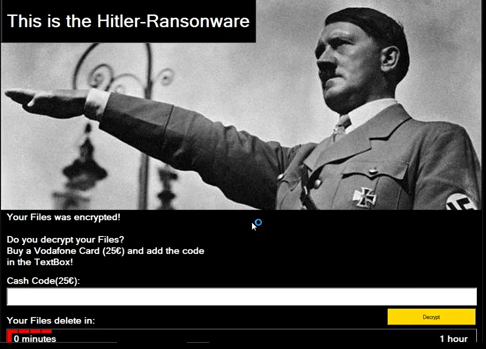 Now you will notice these examples look nothing alike. That is because, each ransomware variant has their own ransom page that comes up after you’ve been infected. However a trend found in each is the words “Your files are encrypted”. If you receive any kind of message stating your files have been encrypted, with a payment demand, you have been hit with ransomware.
Now you will notice these examples look nothing alike. That is because, each ransomware variant has their own ransom page that comes up after you’ve been infected. However a trend found in each is the words “Your files are encrypted”. If you receive any kind of message stating your files have been encrypted, with a payment demand, you have been hit with ransomware.
As we know, ransomware has gained in popularity in the last year. Thousands, if not millions, of computers have been infected with legitimate ransomware attacks, and the victims have paid millions upon millions of dollars to these cyber criminals. By continuing to pay the hackers, the ransomware epidemic will continue.
Ransomware – The Aftermath
Some may ask, why victims pay the ransom when we know it just reinforces the hackers to continue with these attacks. First, retrieving the files from a ransomware attack is incredibly difficult. For a home user, depending on the files, they could possibly wait to see if a decryption tool, a tool to unlock the files, becomes available in the near future. This could take weeks, months or even years. Most people don’t have that kind of time.
Many victims find they are able to restore their computers by either accessing a system restore point, or using backup files to restore their locked data. Unfortunately, this again takes time, which some people don’t have. Thinking of this from a business perspective, the hours it may take to not only retrieve the backup files, but then upload them could be daunting. Also, from a business perspective, they may have to hire a firm to assess the damage, determine the files that were accessed, etc. Again, time and money. So when you look at all of the contributing factors — is it worth just paying the demand and moving on?
No. Not even a little bit. For a few very clear reasons.
- You paid them. Now what is to say they actually send you the tool to unlock your files?
- They sent you the tool to decrypt your files–great! Now you’re a sitting duck. You paid once, and they will assume you will pay again. Wait for the next attack patiently…
- You’ve set a standard. Because you paid the ransom, the cyber criminals are making more money. They now know the more people they infect, the more people that will pay. Example: Company X paid. Home user X paid. Company Y and Z will certainly pay too, so they’ll get infected. Home user Y and Z will also surely pay, so they’ll too get infected. See the trend?
Conclusion
To avoid becoming the next victim to ransomware, there are a few steps PC users must take. First, you need to use a security solution that take a preventative approach. As mentioned earlier, getting your files back after ransomware strikes is incredibly difficult. Therefore, you must be proactive and use an antivirus solution that believes in prevention instead of reaction. You can read the latest Virus Bulletin Reactive and Proactive (RAP) Test results here. The RAP scores are based on how several different antivirus solutions detected various malicious files in both a reactive and proactive fashion. Spoiler alert: PC Matic was the leader in proactive detection with a 99.9% detection rating.
Also, in addition to a proactive security solution, be fully aware of what you are clicking on. Several times ransomware campaigns are sent through email. Before you open an email or attachment, think about what you are doing. These hackers aren’t making millions because they’re bad at what they do. The malicious emails and attachments will look legitimate, which is why you need to think about the following:
- Are you expecting this email/attachment?
- Do you know the sender?
- Is the web address legitimate?
- Are the links sending you to where they say they are? (You can check this by hovering the link WITHOUT clicking it, to see where it will send you.)
- Are the links within the email secure? Meaning, does the URL include https:// (You can check this by hovering the link WITHOUT clicking it.)
And if any of this is in question, contact the sender. When doing so, be sure to obtain their contact information from somewhere other than the email you are questioning. If it truly is a malicious email, and you reply to it, do you believe the hacker will say “ya caught me!!”. No, they won’t. Again, confirm the contact information from the sender from somewhere other than that email.
Good luck, and stay safe!!