By GFI Vipre
The bad news for Detective Mills is “some rogue AV”.
It seems poor old Mr Pitt can’t catch a break, because if he isn’t dealing with serial killers doing amusing and inventive things with deadly sins he has websites like The Brad Pitt Fanclub (bradpittfanclub(dot)org/tmp/go(dot)php) directing users to rogue AV installs – and a box, which is as tenuous an excuse as I need to start making wise with the Se7en cracks.
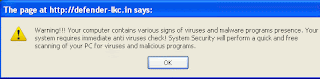
Hitting the above URL will minimise your browser while sending you to defender-lkc(dot)in:
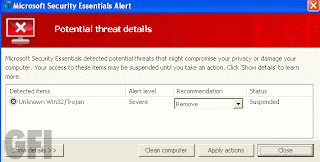
At this point you’ll be offered the box download (well, it looks a bit like a crate but whatever, it’s a box) and opening it up will kickstart an install procedure laced with, oh, at least twenty deadly sins.
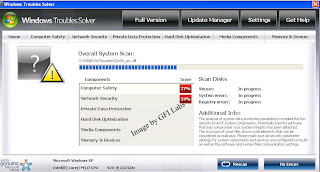
Your final destination is “Windows Troubles Solver”, which is not only a name filled with humorous lies but also a horrible piece of rogue AV which you really should remove as soon as possible.
Current VirusTotal scores are 13/42, and we detect this as FraudTool.Win32.PrivacyCenter.ek!a (v). As a bonus, here’s an interesting Kevin Spacey Se7en factoid.
GFI Vipre Malware Protection Center–Learn More
This post is shared with permission from GFI Vipre.