If you were looking, cyber threats have been in the news for years. However, they’ve been shoved into the limelight over the last few months, between the ransomware attack on the water treatment plant in Florida, Colonial Pipeline, and now Kaseya. The news has left the world wondering what to do to stay cyber secure. What can they possibly include in their security stack to keep their organization from becoming the next headline? Do they need to rip and replace their entire infrastructure in order to strengthen it?
The problem is two fold. First, no one is providing a clear direction on what organizations should be doing. They may share best practices, like timely backups and patch management. But what else? And are these simply recommendations or are they required?
What to do to stay cyber secure
Organizations must be proactive. Timely backups and patch management are important. However, to ensure your digital infrastructure is as secure as possible, you must deploy a default-deny approach to malware detection. This is not a new concept. As a matter of fact there are solutions that have been deploying this method of malware detection for over a decade. However, today there are several vendors who are claiming to use a default-deny approach, like application whitelisting, as a proactive means of malware detection. And they do. However, it is important to understand how.
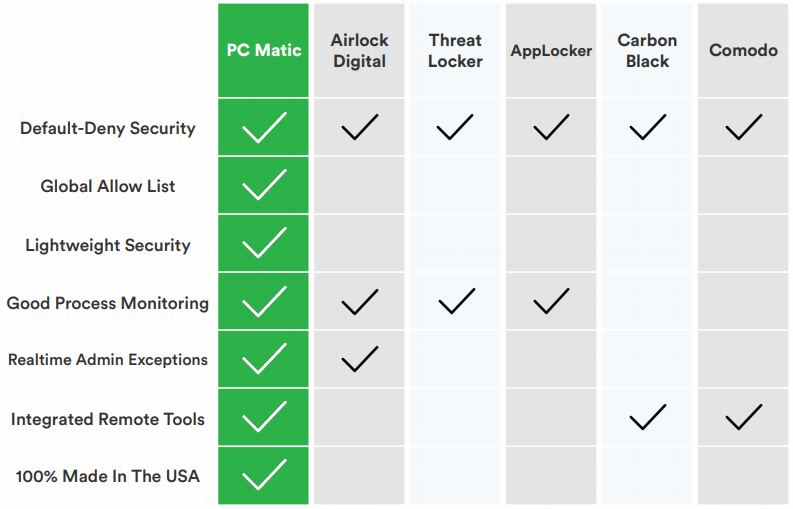
Why is PC Matic Pro Different?
First, and foremost, PC Matic Pro offers an automated global whitelist. This means, IT professionals are not responsible for creating a list of known good applications from the ground up. When PC Matic Pro is installed, the organization uses the automated global whitelist that PC Matic Pro has developed and maintained for the last ten years. Now, let’s touch on that maintained part.
PC Matic has a team of trained, malware research professionals who are responsible for testing each unknown file that tries to execute on any of their customer’s devices. This not only removes the testing burden off of the organization’s IT department, but by moving the heavy analysis to their own servers, PC Matic Pro is able to offer a lightweight agent that pales in comparison to its competition.
Beyond the above, PC Matic Pro offers a dual approach. For organizations looking to replace their existing security solution, they can use PC Matic Pro to cover all of their cybersecurity needs. However, there are other organizations that simply want to layer an application whitelisting agent on top of their existing security stack. PC Matic Pro can do that as well, as it is able to work along side other cybersecurity solutions without causing conflict.
Do I have to?
For many organizations, no, they do not have to take the steps outlined as best practice. However, ethically, they should. Think about this from a consumer, client, employee, or student perspective. They are trusting organizations to keep their data safe. Whether it is personally identifiable information, or a user name and password; customers are trusting companies to keep that information secure. If organizations are not taking the steps to proactively secure it, they are doing a disservice to those who support their company.
Now, as mentioned, a majority of organizations do not have formal cybersecurity regulations to abide by. Although, there are some regulations that fall into place for healthcare facilities. For instance, if a breach occurs and patient data is breached, they are required to notify those individuals. For organizations that work with government entities, they have formal regulations they are expected to follow as well.
Overall, regulations for cybersecurity are lacking. We can preach from the rooftops best practices, but that doesn’t mean they will be followed. Here are five easy to deploy and maintain best practices that PC Matic encourages every organization to have in place:
- Include application whitelisting into your security stack
- Backup your information daily, quite possibly even hourly depending on the size of your organization
- Update operating systems and third-party applications within 48 hours of the update being released
- Change passwords every six months
- Enable multi-factor authentication on the applications and software that already have it included




