The Malware Research team here at PC Pitstop has noticed a large number of hits on seemingly randomly-generated files in our research queue. Upon further investigation, it is apparent that these files are coming from Emotet Banking Trojan. In this post we will give a brief overview of the Trojan, how we detected it, and explain how it is blocked for all PC Matic SuperShield customers.
We noticed files which look like this in our database:
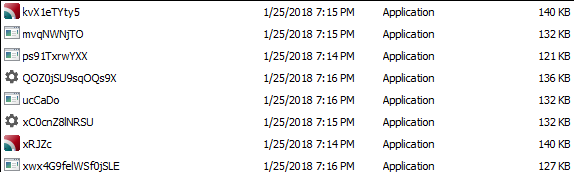
To any human, these files names would seem bizarre and randomly-generated, but the computer has a difficult time recognizing this. As you can see, the files are all around the same file size and have a similar naming scheme, but are slightly different from one another. To a Malware Researcher, this is a giant red flag.
Upon further examination using analysis tools, and dynamic analysis by running the file, it is clear that this is malware. There are not many signs when these files are opened up in a basic static analysis tool such as PE Studio, and when attempting to open in IDA Pro disassembler, there are errors which indicate that the files are perhaps packed. Interestingly though, a typical packed file has a byte entropy reading of 8 but these are only at 5. When using ProcMon and Process Hacker and launching the malware, we do see that it spawns another child process. We were able to dump this child process, entitled servicesec.exe. This allowed us to examine the string data in the file after it was unpacked from its dropper, exposing some strings:
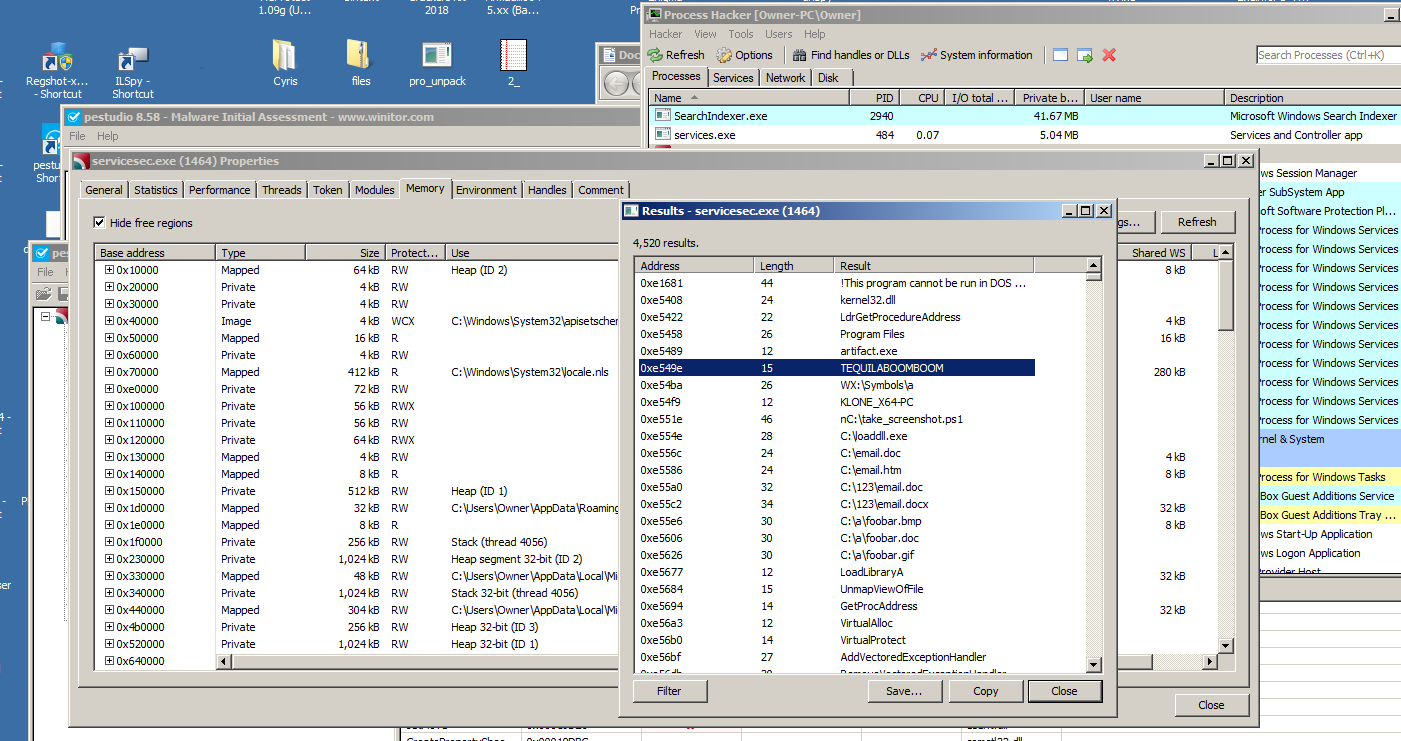
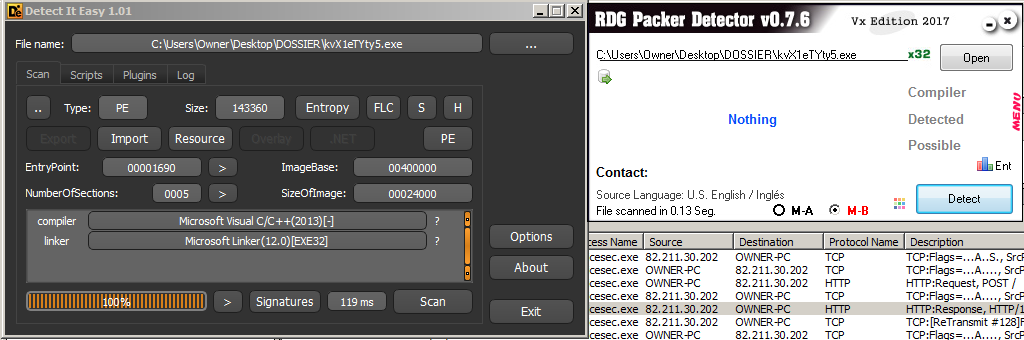
We can see in the process’ in-memory strings there are a few signatures such as TEQUILABOOMBOOM and servicesec.exe itself. If we then Google for “TEQUILABOOMBOOM servicesec.exe malware” we immediately get hits on Emotet Banking Trojan and prior research which describes this exact behavior such as Trend Micro’s analysis and Bromium’s analysis, describing the polymorphic files. Essentially, there is indeed a new executable created with every Emotet infection which prevents any blacklisting-based detection from catching the Trojan, as well as continuously changes the malware’s hashes. This is what was causing tons of hashes to enter our database. Interestingly, if we examine these droppers in PEiD, RDG, or DIE Packer detectors, we are told that the files are not packed. This is because this malware implements its own custom-made packer and therefore does not match any commercially-available packer signatures and goes undetected. The telltale sign that the programs were packed was the lack of imports and useful strings being displayed by PE Studio though. Below is a shot of RDG and DIE both failing to detect Emotet’s custom packing:
Rather than spend a very long time trying to reverse-engineer Emotet’s custom packer in order to extra the malware, luckily, thanks to process dumping tools like Process Hacker, Process Explorer, or even a debugger, we can skip that step and access the malware anyway. This is a useful technique that malware researchers can use to expedite analysis and it will work on packers which do not use a virtual machine protection.
As aforementioned, Emotet is a banking Trojan which means that its goal is to listen to a victim’s keystrokes and browser activity, looking for when a user browsers a site like https://wellsfargo.com or https://www.bankofamerica.com/ , and then steal the victim’s login credentials, sending them to the criminal’s server so that they can steal the victim’s money. Banking Trojans observe network and browser activity, take screenshots, and log the victim’s keystrokes in order to accomplish this.
This Trojan highlights the strength of PC Matic SuperShield because while a polymorphic malware like Emotet can avoid standard AV detection, it actually triggers SuperShield’s whitelisting technology because it continuously generates new files which are all automatically blocked by default.