Locky Encrypts Files Leaving a .Ykcol Extension
A new Locky variant has been released into the wild and upon initial review it led researchers to a believe it was a new strain entirely, called Ykcol. However, after additional review, experts have confirmed Ykcol is another version of Locky.
The email subject line has been confirmed as Status of Invoice. According to Bleeping Computer, within the email there is an 7zip or 7z attachment.
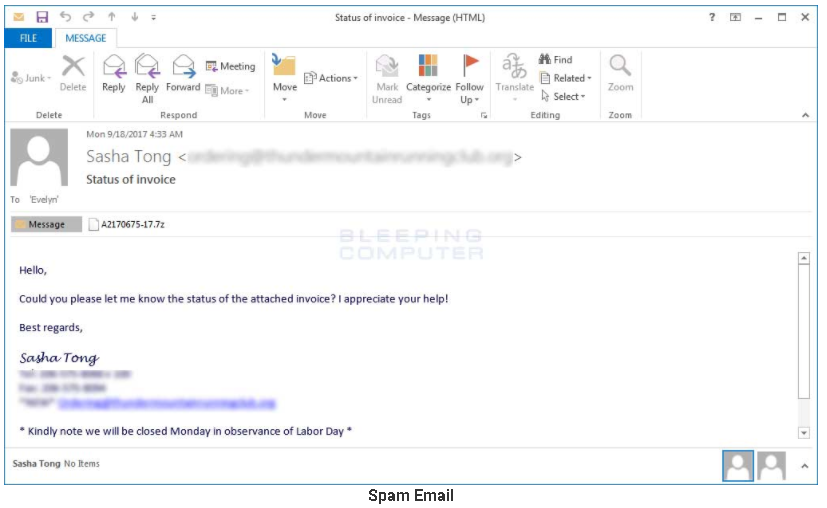
Photo – Bleeping Computer
It is clicking on this attachment that will lead to infection. Therefore, once the attachment has been clicked on, the ransomware goes to work encrypting files. After encryption, it will change the file extension to .ykcol — which is Locky, spelled backwards. The ransom demand is .4 bitcoins, which as of today’s value is equivalent to $1,693.28 USD.
At this time, there is no way to decrypt the infected files for free, leaving only backups as a viable option to recover from this infection.
Prevention is Key
Instead of relying on backups, or the sheer belief of “this won’t happen to me”, PC users are encouraged to do the following:
- Keep your operating system updated
- Ensure all of your programs are updated
- Implement a security solution that implements application whitelisting
- Partake in cyber security training to stay updated on the latest cyber security threats
- Think before you click — Do you know the sender? Are you expecting this email? Never click on something, unless you’re absolutely certain it is legitimate




