By MakeTechEasier.com
4 Simple Steps to Protect Yourself from Phishing
Fishing can be a really enjoyable activity. But, getting fished, or phished for that matter, is not so fun. Yes, it is actually possible for people to get phished. Just like how fish that are fished are lured and killed, people who are phished are deceived and victimized. What exactly is phishing? Phishing is the act of deceiving (usually through email) people to reveal sensitive information such as passwords, bank account numbers, social security number, and credit card information.
With such sensitive information on the line, the stakes are obviously high. Sadly, as dangerous as they are, phishing attacks are common – very common. The 2012 RSA online fraud report indicates that there is an average of 33,000 phishing attacks each month; and these are just the ones reported. Because phishing attacks are so dangerous and prevalent, it is definitely important to protect yourself from them. This guide shows you how phishing attacks work and how to protect yourselves from them.
How Phishing Attacks Work
The main objective of phishing scammers is to steal information. To do this, hackers determine what information they need and how to retrieve it. They usually do this by sending you counterfeit or fake emails that seem to be from a legitimate company like Facebook, Bank of America, and LinkedIn. In a majority of cases, they tell you that you need to update your personal information for security purposes. Here is how one phishing email might look like:
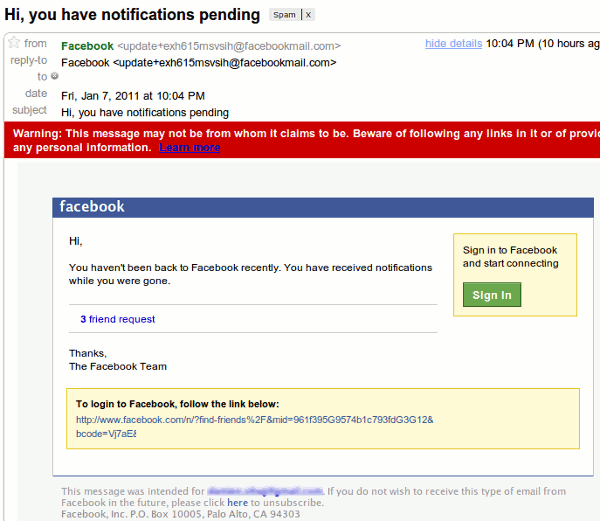
Exceptionally aggressive spammers may even tell you that your account will be permanently deleted if you don’t update your information. Such scare tactics may indeed move you to give out your personal information. This is why many people are victims of identity theft. Here is an example of a phishing attack process:
1. You receive an email that seem to be from a legitimate company.
2. You are told that you need to update personal information for security purposes.
3. Concerned about safety, you click on the link that points to the counterfeit website.
4. You land on a website that looks exactly like the real one.
5. You enter your personal information and attempt to login.
6. The hacker now has your information – you’ve just been phished. You are at the mercy of the “phisherman” or hacker. They can hijack your account, go on a spending spree, or selling your account information in the online black market.
As you can see, it only takes about a minute or less to get hacked. Fortunately, you can protect yourself. Follow these tips below.
How to Protect Yourself – 4 Simple Steps. Article Continued Here
This excerpt is shared with permission from maketecheasier.com.



